Have you inadvertently clicked on a phishing link and now dread the consequences? It’s definitely not a situation to take lightly, but don’t fret. The good news is you can take actions to mitigate, if not completely prevent, the potential damages.
That’s where this guide comes in! We’ll walk you through specific steps you can take to regain control of the situation.
Why clicking on a phishing link is so dangerous?
Before anything else, it’s essential to understand what exactly makes phishing links so dangerous. You can then fully appreciate the solutions that we offer in this guide.
Let’s start with some statistics:
- In 2023, around 30 percent of Internet users around the world fell victim to some kind of phishing attack. That translates to about 1.8 billion people!
- On average, phishing attacks cost businesses around $10.3 billion in financial damages.
- In 2023, there were 800,944 cases of phishing attacks reported to the FBI.
What’s even harder to comprehend is that these statistics are only the tip of the iceberg regarding the damages that phishing attacks can cause. But what makes this cyber threat so distressing is how perpetrators will go to deceive their victims.
Many phishing emails look almost indistinguishable from the legitimate organizations they purport to be. This could be anything from credit card companies, online stores, or—most insidiously— even your own employer. The narrative differs but almost always involves a sense of urgency designed to make you do one simple thing — click the link.
Consider this example of a phishing email designed to steal the victim’s credentials for their Paypal account.
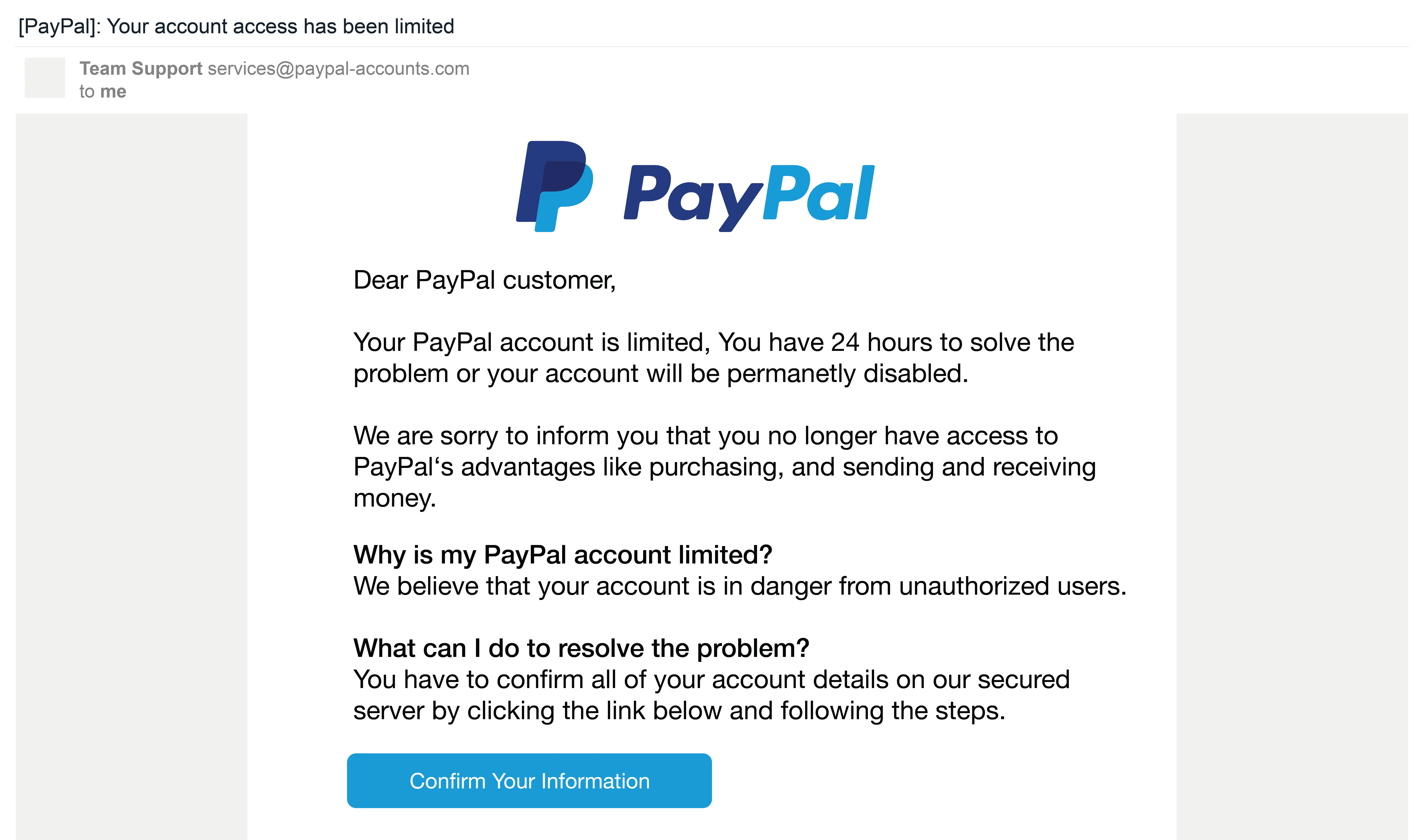
Notice how the email tries to scare the recipient into taking a particular action. Well, that one action is all that phishers need to start siphoning off sensitive information from the potential victim’s online accounts. This includes credit card numbers, email logins, social media accounts, etc.
As you might imagine, clicking on a phishing link can have devastating consequences. It gives cybercriminals all the information they need to execute identity theft and myriad related scams. But beyond financial losses, phishing can cause irreparable damage to one’s personal and professional reputation.
For example, you clicked on a phishing link, so the perpetrator can now access your email. This means the phisher can now impersonate you and email people in your contact list.
What happens if you click on a phishing link?
At this point, you might be wondering what exactly happens after you’ve clicked on phishing email. Here are a few typical scenarios:
- Data harvesting: After clicking on a link, would-be victims are redirected to a page that looks similar to a legitimate source they trust—enough so that they then willingly enter their login credentials—going straight to the phisher.
- Malware distribution: Phishers can use the link to deliver many sorts of malware on a victim’s device. The malware is often a type of spyware designed to steal sensitive data in the background, also known as ransomware.
- Sleeper attacks: Malicious code is introduced to the victim’s device with no noticeable effects at first. However, this type of phishing attack is the most dangerous as it stays with the victim for months, stealing huge amounts of data over a long period of time.
The methods above are but a few examples that outline the sort of damage a phishing attack can cause to your personal or professional life. We cover this not to scare you, but to drive home the fact that it’s a threat every internet user really should take seriously.
Fortunately, there are plenty of things that you can do to avert this disaster, as long as you act fast enough. In the next section, we’ll review a step-by-step playbook you can implement in response to a suspected phishing attack.
What to do if you already clicked on a phishing link?
Before we get into the specific actions you can take after clicking on a phishing link, we’d like to congratulate you for reaching this point alone. Recognizing that you’ve potentially clicked on a phishing link is quite a feat in itself. Most phishing victims do not even realize they’ve been targeted until the damage is done.
What to do after clicking a phishing link: a step-by-step approach
- Take your device offline. The idea is to sever the flow of information between you and the perpetrator of the phishing attack.
- Do a deep scan of your device for any trace of malicious code or malware. A reputable anti-virus program should be able to take care of this step for you.
- Change the passwords on all of your sensitive accounts. Even if you don’t find anything during the malware scan, it’s still possible that sensitive information has already been sent to the phisher.
- Review all of your financial transactions and any unusual activities on your online accounts. If you find any actions you don’t recognize, notify your bank immediately so that they can put a hold on your financial accounts.
- Report the case to all affected parties. This will buy everyone the time they need to secure their respective accounts.
- Learn from the experience. Think about how you got into the situation in the first place and take the events to heart. Remember that the best solution to any problem is to prevent it from happening in the first place.
Again, time is of the essence when dealing with a phishing attack. The sooner you act and complete the steps above, the greater your chances of minimizing any damage.
How phishing attacks can be prevented?
Now that we’ve covered what specific actions you should take after clicking on a phishing link, what about preventive measures? That requires us to be extra vigilant and take the following precautionary measures in our online activities:
- Update your software and operating system. Cybercriminals often take advantage of new software vulnerabilities. Installing the latest updates from software developers will help prevent these exploits.
- Use proven security software on all of your devices. This provides an added layer of security against phishing attacks. Look for specific features such as real-time malware protection, email scans, and automated updates.
- Spread the word. Tell the people around you about your experience with phishing attacks and how they can protect themselves. Phishing relies on internet users’ general lack of awareness, so the more people who know about it, the less effective it will be.
- Always verify. If there’s one rule of thumb that’ll help keep you safe online, it’s that you shouldn’t take anything you see at face value. Take the time to confirm the source of any messages you receive that entail taking a specific action — clicking a link, downloading a file, etc.
- Strengthen your passwords. Ensure all your passwords are unique and contain a long combination of letters, numbers, and special characters.
- Switch to a secure email service with phishing filters that automatically detect and prevent phishing emails from appearing in your inbox. A few good examples of such email services are ProtonMail and SecureMyEmail.
Make it a habit to back up important data. That way, you’ll always have a way to retrieve them in the case of cyber attacks such as viruses and ransomware.
Of course, if you’re serious about your data security and ensuring you’re protected from phishing attacks, then there’s one other tool we recommend adding to your arsenal — a VPN (Virtual Private Network) service!
VPNs add another layer of data security to your online activities by encrypting all data from your device. This prevents phishers from being able to read any data they can steal from your device. VPNs also conceal your real IP address, which makes it more difficult for cybercriminals to target you with a phishing attack in the first place.
And the best part is that VPNs are now fairly easy to use these days. In fact, many premium VPS on the market will get you up and running in just a few minutes. One good example is ClearVPN — a fast and user-friendly Ukraine-based VPN service that works on all popular devices and operating systems.
Specifically, this includes popular operating systems like Windows and macOS and mobile devices such as iPhones and Android smartphones. All you have to do is download the installer for the VPN app, run it, and connect! Also, ClearVPN now has a free 3-day trial, so you can try to use it for free!
Every bit helps when it comes to preventing phishing attacks. With a good VPN service, you can greatly reduce your chances of becoming the next victim and learn how to reduce damage to your finances and/or reputation.
FAQs
Can you get hacked by clicking on a phishing link?
Yes, it’s possible, especially if you provide sensitive information that a hacker could work with. This includes your date of birth, location or login credentials for any of your accounts. Hackers can use phishing to gather information from their victims covertly.
How do I know if a link I clicked is safe?
One quick way to determine whether a link is legitimate is to review its URL structure carefully. If the domain name does not match the organization it’s supposedly from, it’s likely a phishing link.
