In today’s connected world, robust wifi security is more crucial than ever. As we rely on wireless networks for everything from banking to social media, securing these connections from potential threats has become paramount.
In this guide, we’ll go over the evolution of Wi-Fi security protocols, comparing WEP, WPA, WPA2, and the latest advancement, WPA3. By understanding these different protocols, you can ensure that your home or business network is both safe and secure, protecting your sensitive data from malicious intrusions.
What exactly are Wi-Fi security protocols?
First things first — what are wireless security protocols, and why do they matter? Put simply, a security protocol is a set of rules and procedures that govern how data is transmitted over a network.
In the case of Wi-Fi, these protocols are responsible for ensuring that your wireless connection remains secure and encrypted. Without proper security protocols in place, anyone in proximity to your network can intercept and access your data.
For example, when you connect to a public Wi-Fi network at a coffee shop or airport, your device communicates with the wireless router using these security protocols. This allows for secure transmission of data between your device and the internet. However, they come in various types and levels of security, and it’s essential to understand the differences between them.
Types of Wi-Fi security protocols
Now that we have a basic understanding of what Wi-Fi security protocols are, let’s dive deeper into the different types. The most common ones are the following:
- WEP
- WPA
- WPA2
- WPA3
What is WEP?
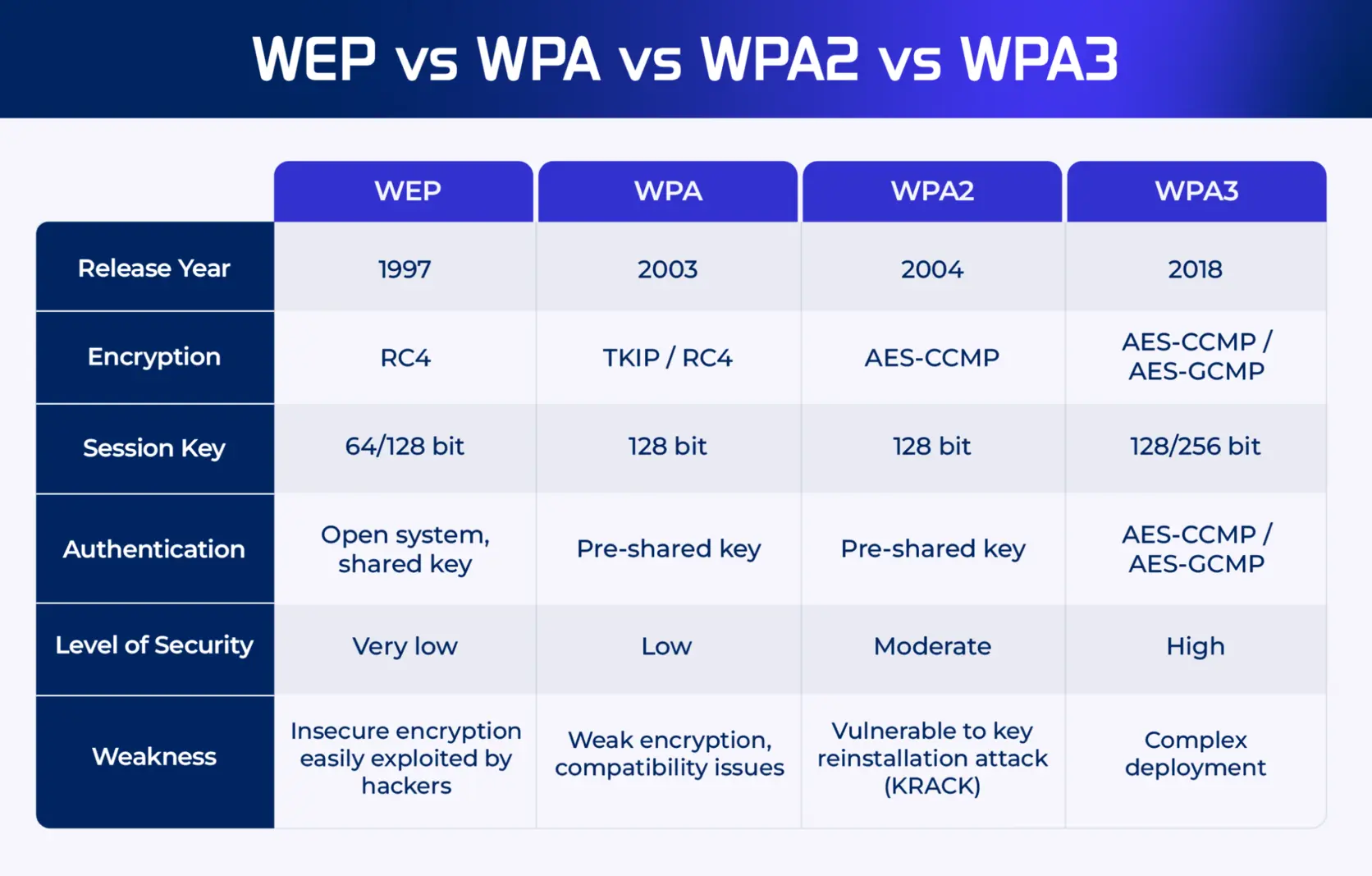
WEP (Wired Equivalent Privacy) was the first wireless encryption protocol introduced in 1997. It was designed to provide the same level of security as wired networks, hence its name, “wired equivalent.” However, it quickly became apparent that this protocol had significant flaws and vulnerabilities that made it easy for attackers to crack.
One of these weaknesses is the use of a static encryption key, which means that all devices connected to the network share the same password. This makes it easier for hackers to intercept and decode the data being transmitted. Additionally, WEP has a small key size, making it more susceptible to brute force attacks.
Despite its flaws, some older devices still use WEP as their only security option. However, it’s highly recommended to upgrade to a more secure protocol if possible.
What is WPA?
WPA meaning “Wi-Fi Protected Access” was introduced in 2003 by the WiFi Alliance after realizing the weakness of WPA. It was quickly launched as an interim solution before the release of a stronger security protocol — WPA2. It addressed many of the vulnerabilities found in WEP by implementing dynamic encryption keys and stronger authentication methods.
However, even with these improvements, WPA is still vulnerable to brute force attacks and has a limited number of possible keys, making it relatively easy to crack.
WPA2: Wi-Fi Protected Access 2
Released in 2004, WPA2 quickly became the gold standard for Wi-Fi security protocols. It addressed the weaknesses of its predecessors by implementing AES encryption, which is considered virtually uncrackable.
Additionally, it also introduced a more secure key management system known as the Pre-Shared Key (PSK) or Personal mode. This means that each device connected to the network has its unique password, adding an extra layer of protection against potential intruders.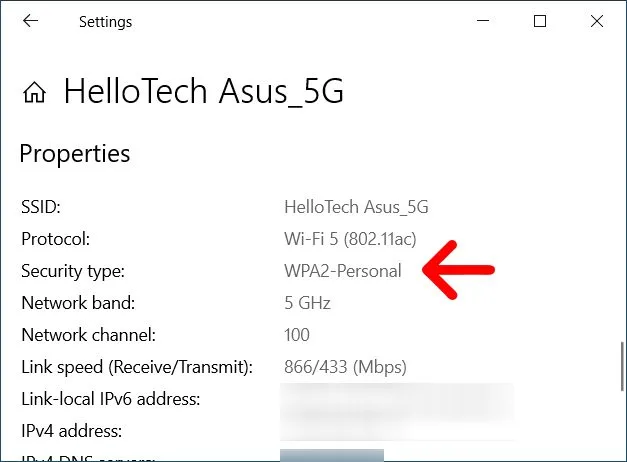
However, WPA2 is not without its flaws. In 2017, a vulnerability known as KRACK (Key Reinstallation Attack) was discovered, compromising the security of WPA2 networks. This highlighted the need for continued evolution and improvement in Wi-Fi security protocols.
WPA3: Wi-Fi Protected Access 3
In response to the weaknesses found in WPA2, WiFi Alliance released WPA3 in 2018, providing even stronger protection against potential attacks. One of its significant improvements is the use of individualized data encryption, meaning that each device connected to a network has its unique encryption key.
Additionally, WPA3 also introduces Simultaneous Authentication of Equals (SAE), which further enhances the authentication process and protects against brute force attacks. While WPA3 is still relatively new, it’s expected to become the next standard in Wi-Fi security protocols and offer even more robust protection for wireless networks.
WPA vs WPA2
While WPA/WPA2 are technically two separate protocols, they are often referred to cumulatively as WPA2. This is because WPA is the precursor and transition phase to WPA2.
In terms of security, WPA2 is significantly stronger than WPA, so it’s always recommended to use WPA2 if possible. However, some older devices may not support WPA2 and will require compatibility with the older protocol.
WPA2 vs WPA3
As mentioned, WPA3 is the latest advancement in Wi-Fi security protocols. While it’s still relatively new and not yet widely adopted, it offers significant improvements over WPA2. With individualized data encryption and enhanced authentication methods, WPA3 provides even stronger protection against potential attacks.
Additionally, WPA3 also addresses vulnerabilities found in public networks by introducing a feature called Opportunistic Wireless Encryption (OWE), which encrypts all network traffic without requiring a password. This makes it safer to connect to public Wi-Fi networks without compromising your privacy.
So which Wi-Fi security protocol should you use?
Now that we’ve gone over the different types of Wi-Fi security protocols, let’s discuss which one you should use. Ideally, you should opt for the most secure option available — WPA3. However, not all devices support this protocol yet, so your best bet would be to use WPA2 with AES encryption, if possible.
If your device only supports WEP or WPA, it’s highly recommended to upgrade to a newer device or router that supports stronger security protocols. In general, it’s essential to regularly update your devices and routers to ensure you have the latest security features and protection against potential attacks.
How to check what security protocol my Wi-Fi is using?
To check what security protocol your Wi-Fi is using, you can follow these steps depending on the device and operating system you’re using.
Windows PC:
- Open Settings:
- Press Windows + I to open the Settings app.
- Network & Internet:
- Click on “Network & Internet“
- Wi-Fi:
- Select “Wi-Fi” from the left-hand menu.
- Network Properties:
- Click on the name of the Wi-Fi network you’re connected to.
- Scroll down to find the “Properties” section. Under “Security type,” you will see the security protocol (WPA2, WPA3).
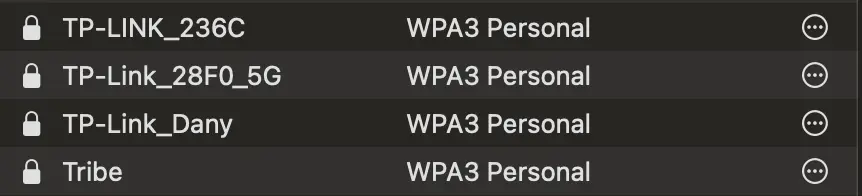
On Mac:
- Open System Preferences:
- Click on the Apple icon in the top-left corner and select “System Preferences“
- Network:
- Next, click on “Network“
- Wi-Fi:
- Select “Wi-Fi” from the list on the left.
- Scroll down and click on the “Advanced” button in the lower-right corner.
- Wi-Fi tab:
- In the Wi-Fi tab, you will see a list of all networks you were connected to and their security protocols.
- In the Wi-Fi tab, you will see a list of all networks you were connected to and their security protocols.
Boost your Wi-Fi security with a VPN
Regardless of what Wi-Fi security protocol you use, it’s always a good idea to take extra precautions to protect your online privacy and security. One way to do this is by using a Virtual Private Network (VPN) when connecting to public or unsecured networks.
A VPN creates an encrypted tunnel between your device and the internet, making it nearly impossible for anyone to intercept or access your data. This added layer of protection is especially crucial when connecting to public Wi-Fi networks, which are often vulnerable to attacks.
You can think of it as another layer of security on top of your Wi-Fi security protocol. It’s an effective way to safeguard your sensitive information and ensure your online activities remain private, regardless of the network you’re connected to. Even if someone were to crack your WPA3 encryption, they would still be unable to access your data due to the added protection of a VPN.
The best part is that it’s surprisingly easy to get started with a VPN service these days. Even if you’ve never used a VPN before, most providers offer user-friendly app that require minimal setup and technical knowledge.
Let’s take ClearVPN, for example — a fast and reliable VPN service that offers a range of features to enhance your online security and privacy. You can start using it with just a few simple steps:
- Download and install the ClearVPN app on your device (supports PC, macOS, Android and iOS).
- Run the ClearVPN app and sign up for an account. A subscription starts at $9.99 per month with an option to prepay for a year ($44.99 per year or $3.75 per month).
- Log on to the ClearVPN network and click on the large circular “quick connect” button in the middle of the app. This will automatically connect you to the nearest and fastest server location.
And that’s it — you now have VPN security protocol acting as a second layer of protection on top of your WiFi security protocol. Now you can browse the web, stream content, and connect to public networks without worrying about potential security threats or privacy breaches.
FAQs
Which protocol is mostly used in Wi-Fi security?
As of now, WPA2 is the most commonly used protocol in Wi-Fi security due to its widespread adoption and strong encryption standards. However, WPA3 is quickly gaining traction as the preferred choice due to its enhanced security features.
Which is better: WPA or WPA2 or WPA3?
WPA3 is the best due to its advanced security features, such as individualized data encryption and SAE. However, WPA2 remains the most widely used because of its strong encryption standards and compatibility. WPA is outdated and less secure compared to the others.
Does WPA3 affect speed?
WPA3 itself should not significantly impact your internet speed. However, improvements in security may introduce slight delays, generally unnoticeable in everyday use. Your overall speed remains more dependent on your hardware and internet service provider than the security protocol used.