When it comes to Malware, no other type is as infamous as that of a rootkit, and for good reason. This type of Malware is capable of embedding itself into a computer’s operating system so well that most users won’t be able to tell the difference. And to make matters worse, it can be extremely difficult to get rid of once it has infiltrated a system.
Now that wouldn’t be so bad if not for the fact that rootkits can be used to gain unauthorized access to a system and cause serious damage to one’s security and privacy. With this in mind, everyone needs to get a good grasp of how it works and what can be done to shield yourself against this malicious threat.
That’s where this quick guide comes in, and we’ll cover everything from what rootkits are, their various types, and what you can do to keep yourself safe. So, let’s get right to it!
What exactly is a Rootkit?
Now, first things first — what exactly is a rootkit?
In a nutshell, a rootkit refers to a class of stealth malware purposefully designed to bypass the security features on a target computer and wrestle control from its users. This makes them particularly dangerous since they can compromise the security of a device/computer without even realizing it.
After a rootkit infects a computer, cybercriminals can use it for nefarious purposes like stealing personal information or even hijacking the system to hurl cyberattacks on other devices. To make matters worse, rootkits can also make subtle changes to an infected system that renders it vulnerable to more dangerous types of malware (ransomware, spyware, trojans, etc.)
So no matter their purpose, rootkits are capable of significant damage to one’s personal data and the system it infects. This highlights the importance of understanding how this type of malware works and what you can do to protect yourself against it.
Types of rootkits
Rootkits can come in many forms, but there are two types that people need to look out for — user-mode rootkits and kernel-mode rootkits.
- User-mode rootkits are malware that’s designed to run on a target computer and disguise itself as an authorized application. It can tamper with the system settings/applications, steal passwords or personal data, or even record keystrokes.
- Kernel-mode rootkits embed themselves deep into the operating system, which makes it very difficult to detect and remove. Hackers who wish to obtain complete control over a target computer usually employ this kind of rootkit.
While there are certainly other types of rootkits out there, these two are the most common and dangerous types of rootkit attacks. They can even be used together, combining their capabilities and multiplying the possible damage they can impose.
For instance, a user-mode rootkit can conceal malicious files from users, while the kernel-mode rootkit infects the operating system to grant unauthorized access to cyber criminals.
How does a rootkit work?
Without getting too technical, rootkits use various techniques to gain access and control of a system. This includes taking advantage of vulnerabilities in the target’s OS, adding malicious codes to system files, modifying registry entries, or even hijacking the target computer’s BIOS (basic input/output system). It all depends on the type of rootkit used and the perpetrators’ goals.
In the case of user-mode rootkits, they often infect systems through malware installations, while Kernel-mode rootkits typically use drive-by downloads (malicious codes that are downloaded and executed automatically after visiting a webpage) or physical access hacks.
Among the most infamous example of a rootkit attack is the Stuxnet worm, which devastated Iran’s nuclear installations in 2010. That rootkit was remarkable because it’s one of the first to combine kernel and user-mode rootkit capabilities to infiltrate and override control of target systems. It also used advanced propagation techniques like zero-day exploits and file-less infections to spread across networks of machines — a feature that made it even more dangerous and difficult to detect.
An investigation of the Stuxnet worm revealed the use of stolen private key certificates from the Taiwanese company RealTek, which allowed the attackers to sign their malicious code and bypass security checks. With these stolen certificates, they could also bypass the digital signature checks used to verify legitimate software.
How to detect a Rootkit
As previously mentioned, rootkits are dangerous because they are expressly designed to remain undetected to average users. Victims of such an attack don’t often realize that their computer is infected until much later after they start experiencing problems like random crashes and degraded system performance.
The good news is that an average person can do many things to detect, remove and guard against rootkit attacks. The first step is to use a good antivirus program that has been proven capable of detecting and removing rootkits.
One such antivirus program is McAfee Total Protection — a comprehensive security suite with rootkit detection and removal capabilities. However, remember that one quick scan may not be enough to detect rootkits. You should run a deep scan with your antivirus program at least once per month.
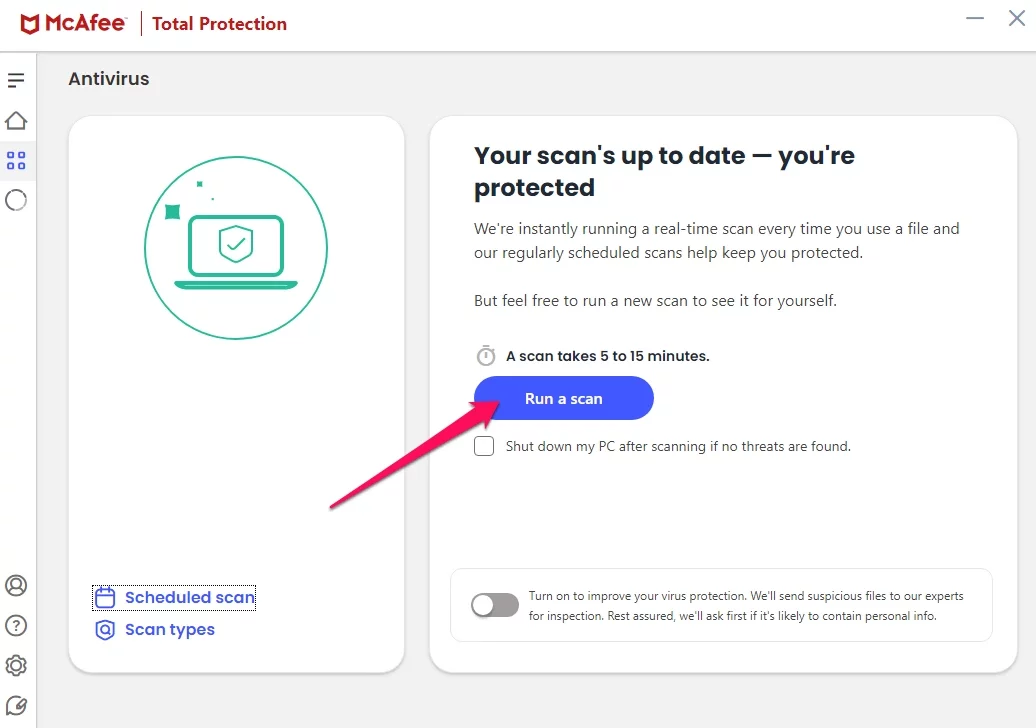
In the case of McAfee Total Protection, you’ll find this option by going to Antivirus > Scan types then clicking on the “Run a scan” button.
Finally, you can also manually search your system for signs of rootkit activity. This includes scouring your computer for suspicious files or programs or checking background processes for functions you don’t recognize. With that said, this option does require some technical know-how, and it’s a very tedious process. So unless you know exactly what you’re doing, it’s best to stick with antivirus software.
How to remove a Rootkit?
So let’s say you’ve detected a rootkit on your system — now what? You’d want to get rid of it right away, and if you detected the threat using an antivirus program, then they normally have additional features in place to remove it for you. Just follow the prompts and complete the malware removal process.
But should you stop there? Well, not quite — as mentioned earlier, rootkits are notorious for leaving behind imprints of malicious code. To be safe, run another full scan until your antivirus software gives you the all-clear.
Of course, if you want to be absolutely sure that you remove all traces of the rootkit from your computer, then there are additional steps that you can take as well:
- Run specialized anti-rootkit programs on your computer. These programs differ from your anti-virus software in that they’re designed to combat rootkits.
- Execute a system restore. If you know exactly when your computer was infected by a rootkit and saved a restore point/backup, then you can run a system restore process that will unwind any changes made to your system.
- Reset and reinstall your computer’s operating system. While this is considered a last resort (this will delete all data from your system and reset your computer to factory settings. That said, it’s the surefire method for dealing with persistent rootkit infections.
Best Rootkit removal software
Among the solutions outlined above, we recommend using a specialized anti-rootkit program as it’s the easiest and quickest method for removing rootkits (aside from using antivirus software). If you have no idea which one to use, then here are some of your best options:
- Malwarebytes Rootkit Remover: One of the most popular and widely used anti-rootkit programs.
- Microsoft Safety Scanner: A free tool from Microsoft that can be used to detect and remove rootkits.
- BitDefender Rootkit Remover: Another popular rootkit removal tool from security experts at BitDefender.
To be clear, anti-rootkit programs are not a replacement for antivirus software. We only recommend them as an additional layer of protection in the fight against rootkits and other types of malware.
What can I do to prevent rootkits from infecting my computer?
Prevention is often said to be the best solution to any problem, and the same can be said about rootkit infections. With that said, here are a few best practices that you can start implementing to keep rootkits at bay:
- Make sure that your operating system is always up to date. The same goes for all the apps/software that you’re running on your computer. This one practice alone can safeguard you from the majority of rootkit attacks.
- Use your anti-virus program to run a full scan on your computer at least once a week and keep it updated with the latest virus definitions. If you can automate both processes, then all the better.
- Avoid downloading anything from untrusted sources. This is the most common method by which rootkits infiltrate a computer system.
But suppose you’re truly serious about keeping your computer safe from rootkits. In that case, we recommend taking your online security to the next level by using a good VPN (Virtual Private Network) service. VPNs help protect against rootkits by encrypting your internet traffic and routing it through a secure tunnel. This makes it practically impossible for rootkits to gain access to your computer.
And you can start doing that with ClearVPN — a VPN service that is simple, secure, and lightning-fast. ClearVPN allows you to instantly access your desired content while protecting your computer from rootkits and other online threats.
Here’s how to get started:
- Go to the ClearVPN website, and click on the “Download for free” button. This will download the ClearVPN installer on your computer. Also, you can download the ClearVPN app from the App Store or other stores for your device.
- Run the downloaded file and follow the instructions to complete the installation process.
- Once installed, launch ClearVPN and create an account (you can do this for free with limited features). You can then log on to the VPN service using your account information (email address and password).
- Select “Smart Connection” for protection.
- Under “Pick Priority”, select “Top Protection“.
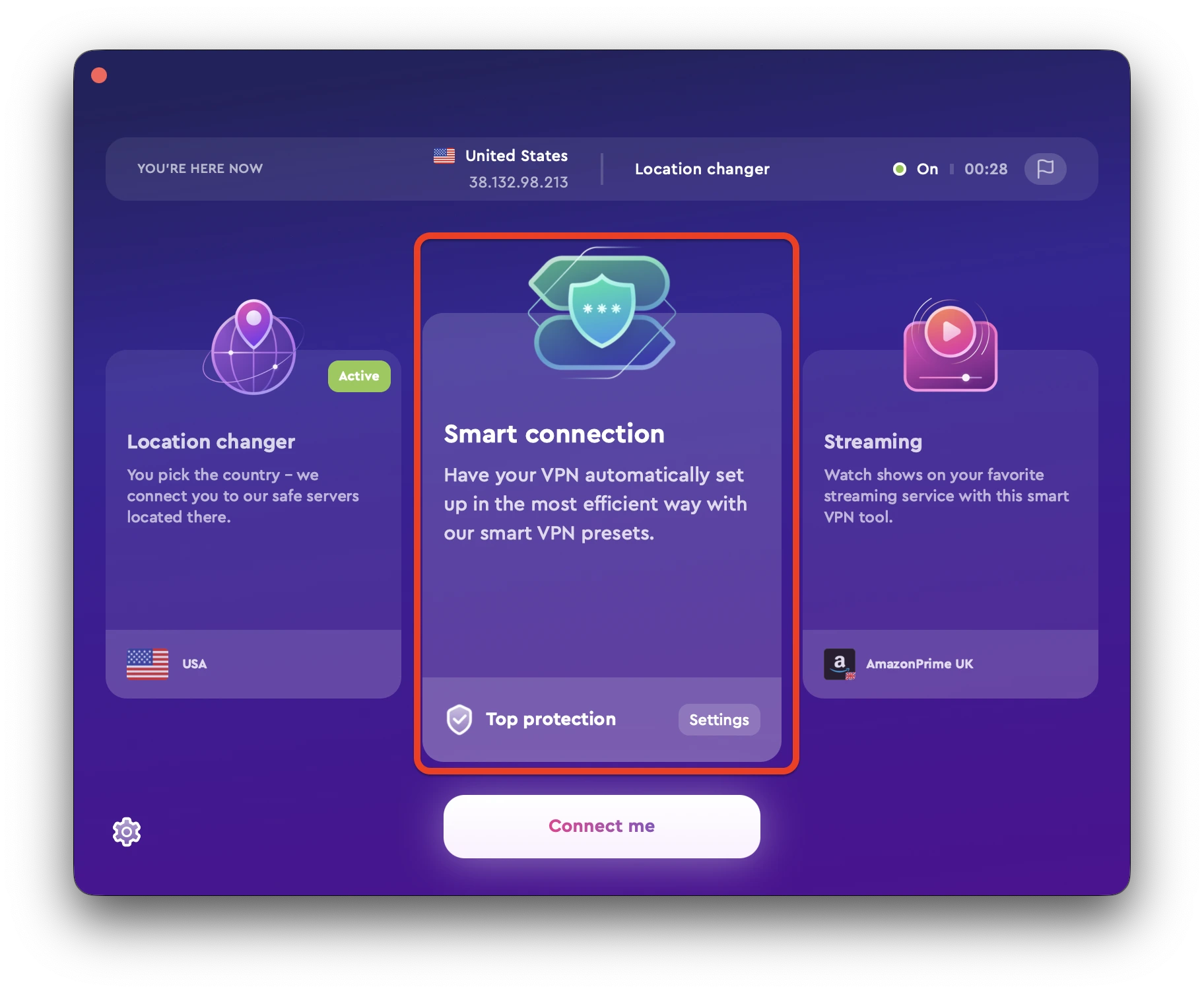
And that’s it — your connection is now secure and safe from rootkit attacks! Keep these best practices in mind, and you’ll be able to drastically reduce your chances of becoming a victim of rootkit malware.
