The fight against malware is always evolving. As soon as one type of malware is defeated, another emerges to take its place. Fileless malware is the latest threat to computer systems around the world and it has become so sophisticated that even the most well-protected systems are vulnerable.
According to a recent report by Watchguard (a security firm), fileless malware attacks increased by 888% from 2019 to 2020, and that figure is only expected to rise in the coming years. Considering how dangerous this type of malware is, it’s important to understand what fileless malware is and how you can protect yourself against it.
Types of malware
Now before we dive into fileless malware, let’s take a step back and understand the different types of malware that exist. This will help to put fileless malware into perspective and understand why it’s such a threat.
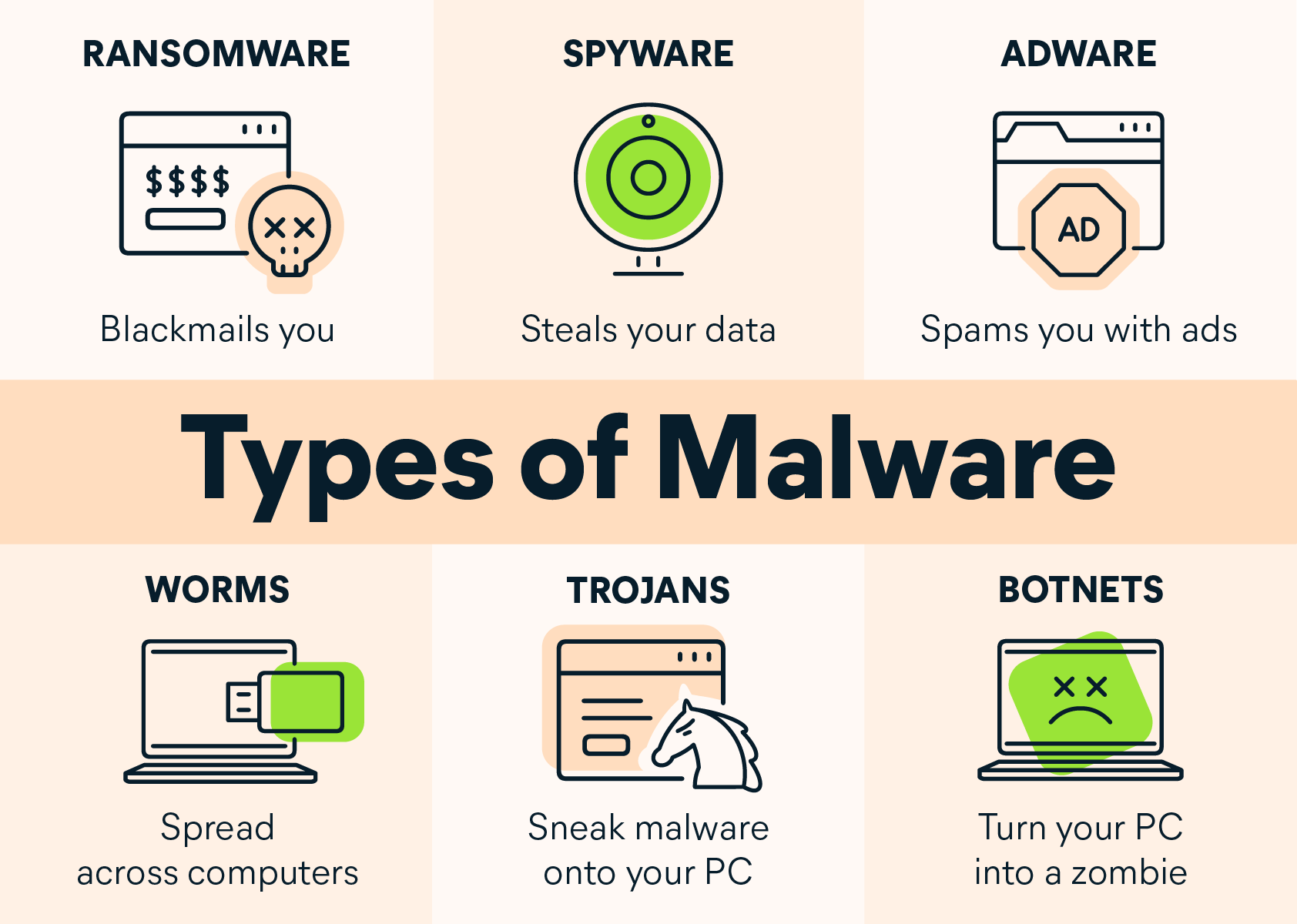
There are six main types of malware:
- Botnets – it is a group of connected devices that are controlled with a bot herder to launch attacks on networks to crush them.
- Worms – A worm is similar to a virus in that it replicates itself, but it doesn’t need to attach itself to a program or file. Worms can infect systems through networks and cause damage.
- Trojans – A Trojan is a type of malware that disguises itself as a harmless program or file, but once it’s executed, it can wreak havoc on a system.
- Ransomware – Ransomware is a type of malware that encrypts files and demands a ransom be paid to decrypt them.
- Spyware – is a malicious software designed to enter your device, collect the data about you and forward it to a third-party without your agreement.
- Adware – or advertising supported content, is designed to display unwanted ads(or pop-up ads) on your devices.
The thing about fileless malware is that it can be any of the above types of malware. For example, a fileless virus would be a virus that doesn’t rely on files to infect a system. It can also behave like ransomware (most common) and encrypt files or like a worm and spread itself through networks. The only difference is that this malware doesn’t need to rely on files to infect a system (hence the name).
Now that we’ve reviewed the different types of malware, let’s take a closer look at fileless malware and why it’s so dangerous.
What is Fileless Malware?
Fileless malware is a type of malicious software that doesn’t rely on traditional methods, such as downloading and installing files, to infect a computer. Instead, it takes advantage of vulnerabilities in existing programs or the operating system to infect a machine.
While fileless malware has been around for years, it has seen a recent uptick in popularity among cybercriminals. One of the reasons for this is that traditional antivirus programs are not designed to detect or block fileless malware, making it a very effective way to infect computers.
One of the most dangerous things about fileless malware is that it’s very difficult to detect. Since it doesn’t rely on files, traditional antivirus programs are ineffective against it. Fileless malware can also avoid detection by using legitimate programs that are already whitelisted by security systems.
Fileless malware is often delivered through phishing emails or other social engineering techniques. Once the malware has been executed, it resides in the system’s memory and starts to collect information or perform other malicious activities.
Notable cases of fileless malware attack
- In 2017, the NotPetya fileless malware attack wreaked havoc across the globe, causing billions of dollars in damage. The attack used a malicious piece of code that was disguised as a legitimate update for a Ukrainian tax software program. Once installed, the malware encrypted hard drives and prevented victims from accessing their files.
- In 2018, the United States government revealed that russia had used fileless malware to target American energy companies. The malware was used to gain access to industrial control systems, which could have allowed attackers to cause a power outage.
- In 2019, the Sodinokibi (also known as REvil) ransomware used fileless malware to infect computers. The ransomware encrypted victims’ files and demanded a ransom be paid in order to decrypt them.
How to get rid of fileless malware?
There are a few ways to get rid of fileless malware. One is to use a reputable antivirus program that has been proven to detect and remove this type of malware. In particular, McAfee’s Total Protection and Norton’s Security Suite are two programs that have been effective against fileless malware.
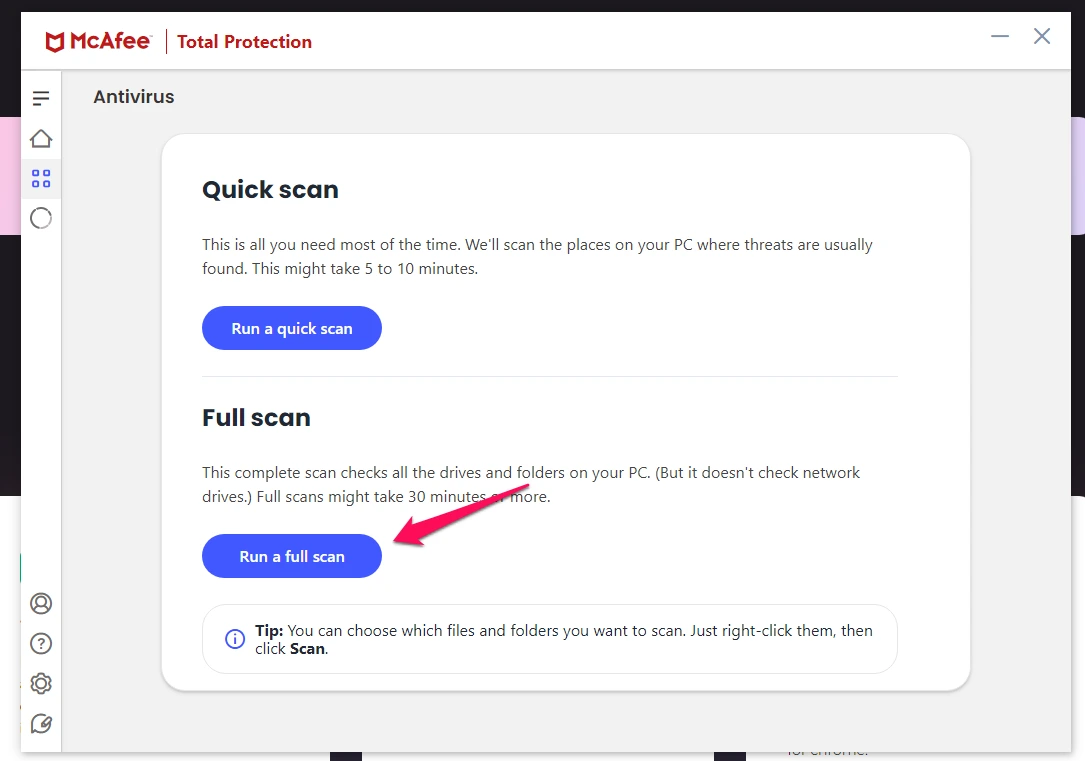
One thing to note though is that you should regularly perform a full scan of your system as opposed to a quick scan. This is because fileless malware can be very difficult to detect and may not be caught by a quick scan.
Another way is to use a specialized tool that is designed specifically for this purpose. One such tool is Malwarebytes Anti-Malware. This type of program is designed specifically to remove malicious software from your computer.
Finally, you can also try using a system restore point to remove fileless malware. This will return your computer to a previous state before the malware was installed. However, this method is not always effective and may not work on all types of fileless malware.
How to protect against fileless malware
When it comes to fileless malware protection, it is well worth pointing out that its spread primarily through social engineering. Cybercriminals will use various methods in order to trick users into installing the malware onto their systems.
This is why it is important to exercise caution when opening email attachments or clicking on links from unknown sources. In addition, you should always keep your operating system and other software up to date as this can help close any vulnerabilities that could be exploited by fileless malware.
It is also a good idea to back up your data on a regular basis. This way, if your computer does become infected with fileless malware, you will not lose any important files or data.
And finally, you should consider using a VPN (Virtual Private Network). This will encrypt your traffic and help to protect your privacy online. Using a VPN can also help to prevent fileless malware from infecting your system as it will make it more difficult for cybercriminals to target you.
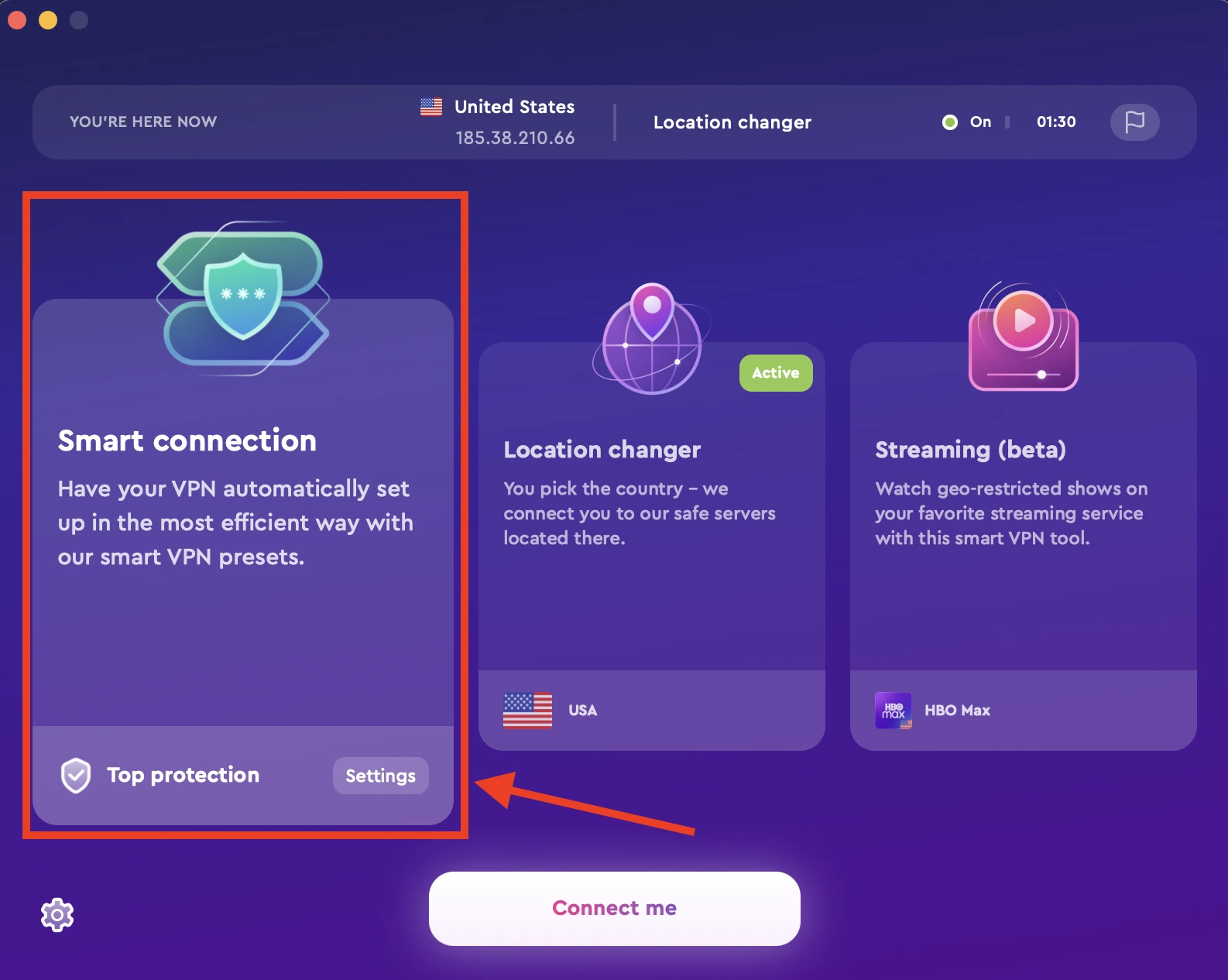
Of course, not just any VPN will do. You should make sure to choose a reputable VPN service that uses strong encryption and has a good privacy policy. We recommend ClearVPN as it meets all of these criteria and more. Plus, it’s extremely easy to use, with one-click shortcuts that will make it a breeze to connect to the fastest server available. Download ClearVPN app and protection and privacy in a click. Here is how to do this:
- Download and install ClearVPN app on you device.
- Run the app and log in to the app.
- Choose Smart Connection mode and click on “Connect me” button – That’s all, now your connection is protected from most of the cyber threats.
FAQs
How does fileless malware work?
Fileless malware usually starts with some sort of social engineering attack in which the user is tricked into executing a malicious payload. Once the payload is executed, it will use legitimate programs and system resources in order to infect the computer.
How can I protect myself from fileless malware?
There are a few things you can do in order to protect yourself from fileless malware. Firstly, you should exercise caution when opening email attachments or clicking on links from unknown sources. In addition, you should keep your operating system and other software up to date in order to close any vulnerabilities that could be exploited by fileless malware. Finally, you should consider using a reputable antivirus program that offers protection against this type of malware.
What should I do if my computer is infected with fileless malware?
If your computer is infected with fileless malware, you can try using a specialized tool to remove it. Alternatively, you could try using a system restore point to return your computer to a previous state before the infection occurred. However, this method is not always effective and may not work on all types of malware.
