Did you know that 95% of HTTPS servers are vulnerable to a man in the middle attack? This includes popular sites like Amazon and Facebook.
What this means for the average Internet user is that your personal data and information such as your security numbers, credit card details, and more are at risk of being stolen by cybercriminals.
In this quick guide, we’ll show you what a man-in-the-middle attack is and how you can protect yourself from becoming a victim.
What is man in the middle attack?
In order to protect yourself from a man in the middle attack, it’s important to first understand what this type of cyberattack is.
A man in the middle attack (MITM) is one where a cybercriminal intercepts communication between two parties and pretends to be one of the parties in order to gain access to sensitive information.
For example, let’s say you’re trying to log into your online banking account. An attacker could intercept the communication between you and the bank’s server. The attacker would then pretend to be the bank and send you a fake login page. If you enter your username and password on this fake login page, the attacker now has your credentials and can access your account.
How does a man-in-the-middle attack work?
Now that you know what a man in the middle attack is, let’s take a look at how this type of cyber attack works.
Without getting too technical, there are three main ways that a man in the middle attack can be carried out:
DNS spoofing
DNS spoofing is the most common type of man in the middle attack. This is where the attacker intercepts communication between the victim and the DNS server. The attacker then alters the DNS records so that the victim is directed to a fake website that looks identical to the real website.
ARP poisoning
ARP poisoning is another common type of man in the middle attack. This is where the attacker sends falsified ARP (Address Resolution Protocol) messages to the victim’s computer. These messages trick the victim’s computer into thinking that the attacker’s computer has the same IP address as the real server.
As a result, the victim’s computer will send all traffic intended for the real server to the attacker’s computer instead. The attacker can then intercept this traffic and access sensitive information.
SSL/TLS spoofing
SSL/TLS spoofing is a less common type of this kind of attack, but it’s still something that you need to be aware of. This is where the attacker intercepts communication between the victim and the server. The attacker then alters the SSL/TLS certificate so that it appears to be from a trusted source.
If the victim then goes to the fake website and enters their login credentials, the attacker now has access to their account.
How to detect a man in the middle attack?
Now that you have an idea of how man in the middle attacks work, you might be wondering how you can detect if you’re being targeted by one.
There are a few signs that you can look out for:
- An unexpected email or text message from a service that you use — You receive an unexpected email or text message from a company that you do business with. The message contains a link to what looks like the company’s website. However, the link is actually to a fake website that’s been created by the attacker. For example, you might receive an unexpected email stating that your password is about to expire or your login.
- You’re redirected to a different website — You try to log in to your online account but you’re redirected to a different website. This is usually a sign that your DNS records have been tampered with and you’re being targeted by a DNS spoofing attack.
- You receive a warning message on your screen — You see a warning message from your browser or antivirus software. This warning message means that the SSL/TLS certificate on the website that you’re trying to visit is not valid. This is usually a sign that you’re being targeted by an SSL/TLS spoofing attack.
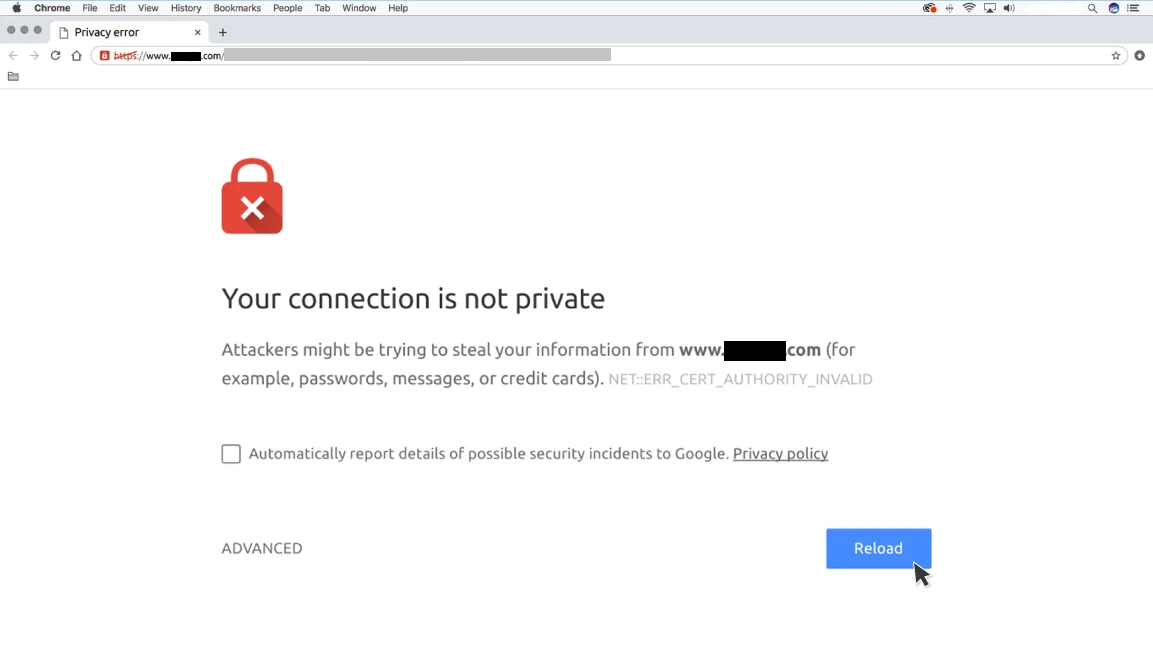
Perhaps the most difficult part of detecting a man in the middle attack is that there might not be any outward signs that you’re being targeted. In many cases, attackers are able to carry out these attacks without the victim ever knowing.
How to prevent man in the middle attack?
Given the covert nature of man in the middle attacks, it’s important to take steps to protect yourself from this type of cyber attack.
Here are a few things that you can do:
- Install a reputable antivirus program on your computer and keep it up to date. Antivirus software can help to detect and block man-in-the-middle attacks.
- Only use trusted Wi-Fi networks. Avoid using public Wi-Fi networks as they are often not secure.
- Look for the padlock icon in your browser’s address bar. This icon indicates that SSL/TLS is being used to encrypt communication between your computer and the website.
- Check that the URL of the website you’re visiting is correct. Be wary of typosquatting, which is where attackers create fake websites with similar URLs to real websites. Check the URLs carefully because sometimes the actual site can look identical.
For example, instead of amazon.com, it might be “amaizon.com” or “amazin.com”
How to prevent man in the middle attack on public Wi-Fi
Now it’s not to say that you absolutely shouldn’t use public Wi-Fi. These networks can prove to be very useful, especially when you’re out and about.
However, it’s important to take steps to protect yourself when using these networks. One of the best ways is to start encrypting your internet traffic so that even if someone does manage to intercept it, they won’t be able to read it.
You can do that with a good premium VPN (Virtual Private Network) like ClearVPN. A VPN encrypts your internet traffic and routes it through a secure server. This makes it much more difficult for attackers to carry out man-in-the-middle attacks.
Most premium VPNs are extremely easy to use and don’t require any technical knowledge. All you need to do is install the VPN software on your device and then connect to one of the servers. In the case of ClearVPN, they have quick shortcuts that make it easy to accomplish whatever you’re trying to do online.
For example, if you want to securely browse the internet, you can just tap/click on the Connect Me button next to the “Smart Connection” mode.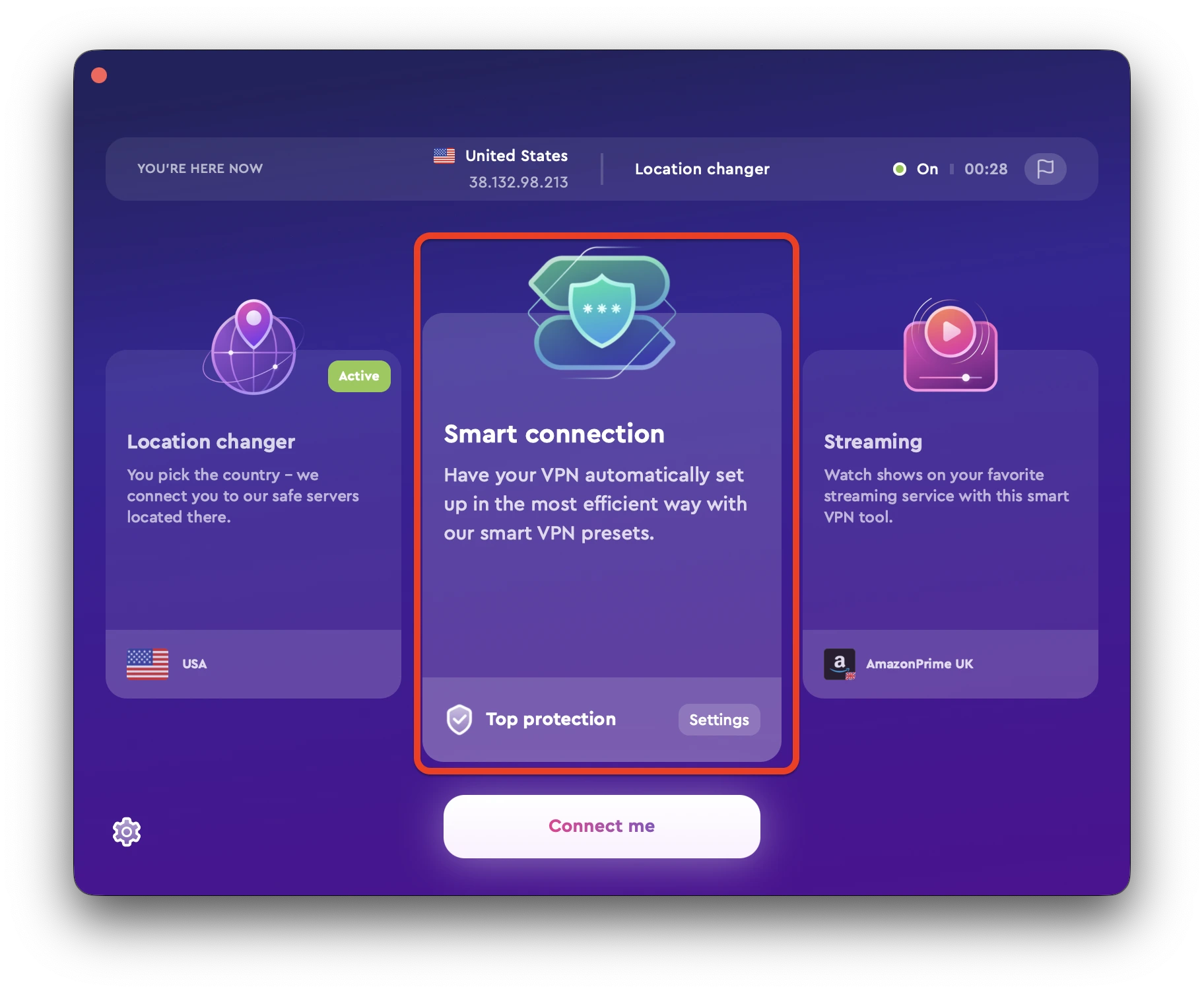
It might seem like a hassle to have to use a VPN all the time. However, it’s a small price to pay for the peace of mind that comes with knowing that your data is safe and secure.
FAQs
What are the dangers of a man in the middle wifi attack?
A man-in-the-middle attack can be very dangerous as it can allow attackers to intercept and read your data. They can also inject malicious code into websites, which can be used to infect your computer with malware.
How common are man-in-the-middle attacks?
Man-in-the-middle attacks are quite common, especially on public Wi-Fi networks. However, they can also be used to target individuals or businesses.
How does a VPN help protect against man-in-the-middle attacks?
A VPN can help protect against man-in-the-middle attacks by creating a secure, encrypted connection between your device and the VPN server. This means that even if someone is able to intercept your data, they will not be able to read it or make any changes.
