In our rapidly evolving digital world, protecting your online accounts and personal information is more crucial than ever. One powerful tool at your disposal is multi-factor authentication (MFA). This is a robust security measure that significantly reduces the risk of unauthorized access to your accounts.
In this quick guide, we’ll explore the ins and outs of MFA, such as its benefits, techniques, and how it distinguishes itself from two-factor authentication (2FA). Moreover, we’ll check out some popular MFA software solutions and additional strategies for enhancing your online security.
Let’s get started!
What is multi-factor authentication?
In brief, MFA is an advanced security measure that demands users present at least two independent credentials to confirm their identity before gaining access to an account or system.
These credentials generally come from five distinct categories:
- Something you know (e.g., password or PIN)
- Something you have (e.g., mobile device or security token)
- Something you are (e.g., fingerprint or facial recognition)
- Someplace you are (e.g., location-based authentication)
- Time (e.g., a time limit for users to complete authentication)
By merging multiple credentials from these different categories, MFA forms a solid authentication process that significantly lowers the chances of unauthorized access. Even if a cybercriminal manages to crack one credential, they would still need additional factors to break in.
Benefits of Multi-Factor Authentication
So, why should you care about MFA, you ask? We live in a digital era where online threats are constantly evolving. By adopting MFA, you’re taking a proactive approach to safeguard your valuable data and personal information.
In this section, we’ll delve into some of the most significant advantages that MFA offers in terms of cybersecurity:
Boost Account Security
The primary benefit of MFA lies in the enhanced security it delivers. By demanding multiple credentials for authentication, it becomes significantly tougher for cybercriminals to gain unauthorized access.
Imagine a scenario where an attacker acquires a user’s password – they still wouldn’t be able to break in without the additional authentication factors. These could range from a one-time code sent to the user’s mobile device or a unique access token that requires scanning.
Minimize Password Dependence
Relying solely on passwords to secure your accounts is often inadequate. They can be easily cracked, guessed, or stolen through phishing attacks, leaving your personal information exposed. MFA reduces password dependence by introducing extra layers of security requiring additional credentials.
Comply with Industry Regulations
Several industries, such as finance and healthcare, enforce strict data protection regulations that mandate organizations to implement robust security measures. MFA enables organizations to meet these requirements by adding an extra layer of authentication.
Enhance User Experience
Although it might seem counterintuitive, MFA can elevate the user experience. By employing biometric authentication methods like fingerprint or facial recognition, users can swiftly and effortlessly access their accounts without memorizing complex passwords.
Multi-Factor Authentication Methods
Now that we’ve covered the basics of MFA, let’s dive into some popular methods for implementing multi-factor authentication. Each method has pros and cons, so it’s essential to find the one that best suits your needs.
SMS-Based Authentication
With this approach, users get a unique one-time passcode (OTP) sent as a text message to their mobile devices. Users must input this code as well as their password to access their account.
Though convenient, SMS-based authentication can be vulnerable to SIM-swapping attacks and interception. However, it remains a widely-used MFA authentication method due to its ease of use and low implementation costs.
Authenticator Apps
Apps like Google Authenticator or Microsoft Authenticator generate time-sensitive OTPs on your smartphone. To access their accounts, users must input the current OTP displayed on the app and their password.
This method is more secure than SMS-based authentication because it doesn’t rely on external networks to deliver OTPs. Additionally, it’s much harder for attackers to intercept or spoof since OTPs are generated locally. On the flip side, it may be less convenient since users need to open the app and enter the code promptly to access their accounts.
Hardware Tokens
These physical devices create OTPs or use a cryptographic key for authentication. Users must have the token and input the generated code or connect the device to their computer to gain access. While highly secure, this method can be inconvenient if the token is lost or damaged.
Biometric Authentication
Biometric methods like fingerprint or facial recognition utilize unique physical traits to verify a person’s identity. These methods are highly secure and user-friendly, as they don’t require users to remember passwords or carry additional devices. However, they may be influenced by environmental factors and necessitate specialized hardware.
Popular Multi-Factor Authentication software solutions
Now that you’re well-versed in MFA and its components, let’s explore some popular tools you can use to implement multi-factor authentication.
Okta
As a leading cloud-based identity and access management solution, Okta offers robust multi-factor authentication options. With support for various authentication methods like SMS, voice call, push notifications, and biometrics, Okta allows you to tailor your MFA experience to meet your needs.
Authy
Authy is a user-friendly MFA app that generates time-sensitive one-time passcodes on your smartphone. Compatible with numerous online services, Authy provides a simple yet secure way to safeguard your accounts. With features such as encrypted backups and multi-device support, Authy is an excellent choice for those seeking a convenient and dependable MFA solution.
SecurID
RSA SecurID is a well-established MFA solution offering both hardware and software tokens and risk-based authentication. Its flexible deployment options and support for various authentication methods make it an attractive choice for organizations of all sizes.
LastPass
While primarily known as a password manager, LastPass also delivers multi-factor authentication capabilities. By integrating with various MFA providers, LastPass enables you to add an extra layer of security to your password vault and other supported services.
Microsoft Authenticator
Microsoft Authenticator is a versatile app that supports multiple MFA methods, including push notifications, biometrics, and one-time passcodes. Its integration with Microsoft services and other third-party applications ensures a seamless experience across your digital ecosystem.
Difference between 2FA and MFA: a quick comparison
You may have heard of two-factor authentication (2FA) and wondered how it differs from multi-factor authentication. It’s a great question, as both terms are often used interchangeably in conversations of online security. Let’s quickly compare the two to help clarify their distinctions.
Two-factor authentication is actually just a subset of multi-factor authentication. While both security measures aim to protect your digital accounts by requiring multiple credentials for authentication, the primary difference lies in the number of factors involved. As the name suggests, 2FA uses precisely two factors to verify a user’s identity. On the other hand, MFA can apply two or more elements, providing a stronger layer of security.
For instance, imagine you’re logging into your email account. With 2FA enabled, you may be asked to provide your password (something you know) and a one-time passcode sent to your mobile device (something you have). In this case, you’re using precisely two factors to authenticate your identity.
Now, let’s say you work for a company that requires an even higher level of security. They might implement MFA, which could involve entering your password, receiving a one-time passcode on your mobile device, and scanning your fingerprint (something you are) before granting access. In this scenario, you’ve employed three distinct factors as part of the authentication process.
Elevate your online privacy with a VPN
Are you looking to take digital security to the next level? Then consider using a Virtual Private Network (VPN). Combining multi-factor authentication with a reliable VPN provider can effectively reduce your digital footprint and ensure that your data is always protected.
A VPN works by encrypting your data as it travels across the internet, making it virtually impossible for anyone to intercept and access your sensitive information. It also masks your IP address, giving you an extra layer of anonymity while browsing online.
Best of all, using a VPN need not be difficult, and you can quickly begin with ClearVPN — a fast, reliable, and user-friendly VPN service — in just three easy steps:
1. Download and install the ClearVPN app from the website. Click the “Download for Free” button and run the installer. You can also search for the app on the App Store or Google Play Store (if you’re on an iOS or Android device)
2. Run the ClearVPN app and create an account to log in. Select the “Create” option or use any social login button — Google, Facebook, or Apple ID.
3. Log in to the ClearVPN app using your account credentials. Select “Smart connection” and click/tap on the “Connect me” button.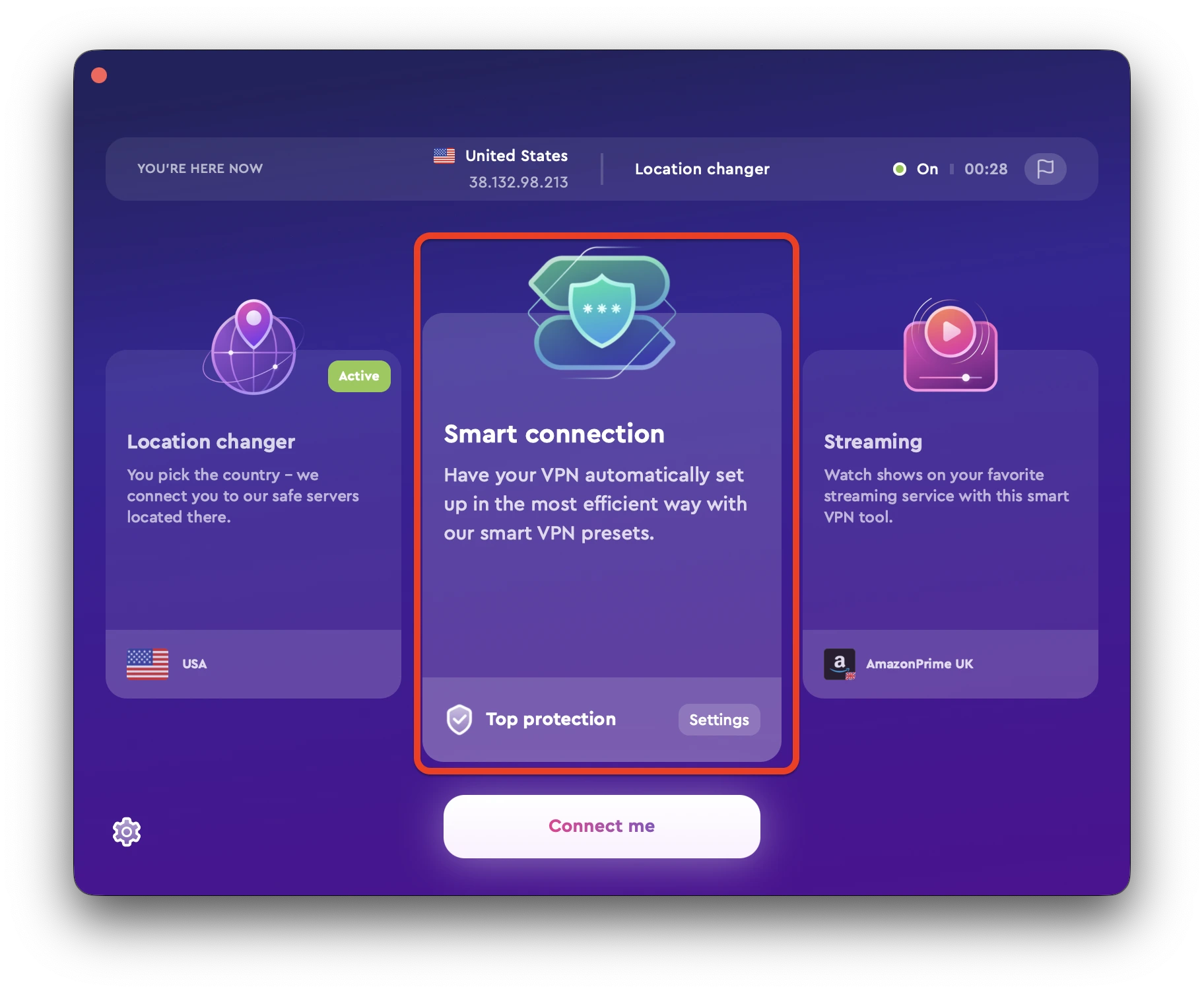
At this point, your connection is now secure. Your internet traffic will now be routed through a VPN tunnel, protecting your data from hackers and malicious actors. It’s that easy!
FAQs
Is multi-factor authentication foolproof?
While MFA significantly enhances account security, no security measure is entirely foolproof. It’s essential to stay vigilant and follow best practices, such as strong passwords, keeping software up-to-date, and being cautious of phishing attacks.
Can I use MFA on all my accounts?
Many online services now offer MFA as an optional security feature. However, not all platforms support MFA. Be sure to check each service’s security settings to see if MFA is available and enable it whenever possible.
Can hackers get past MFA?
While MFA significantly enhances security by requiring multiple forms of verification, no system is entirely foolproof. However, using MFA drastically reduces the likelihood of unauthorized access.
