As the technological landscape continues to evolve, so do the ways in which criminals can exploit vulnerabilities. One of the most common and effective methods used by hackers is social engineering.
According to a recent report by Verizon, social engineering was the root cause of 82% of data breaches in early 2022. This is a dramatic increase from the previous year, in which social engineering was only responsible for 56% of data breaches.
One notable example of social engineering frauds is the recent social engineering attack on Robinhood (a stock trading app). In this attack, hackers used social engineering techniques to steal millions of PII (Personally Identifiable Information) from Robinhood users.
And that’s just one example. Social engineering attacks are becoming more and more common, and they’re only getting more sophisticated. It’s only natural to wonder: what is social engineering and how can I protect myself from it?
So what is social engineering?
In simple terms, social engineering is the act of manipulating people into performing actions or divulging confidential information. Criminals can use social engineering to gain access to physical locations, systems, and sensitive data. They can also use it to spread malware and perform other malicious activities.
How does social engineering work?
Criminals use a variety of techniques to perform social engineering attacks. They may pose as a trusted individual or organization, send phishing emails, or even use physical intimidation.
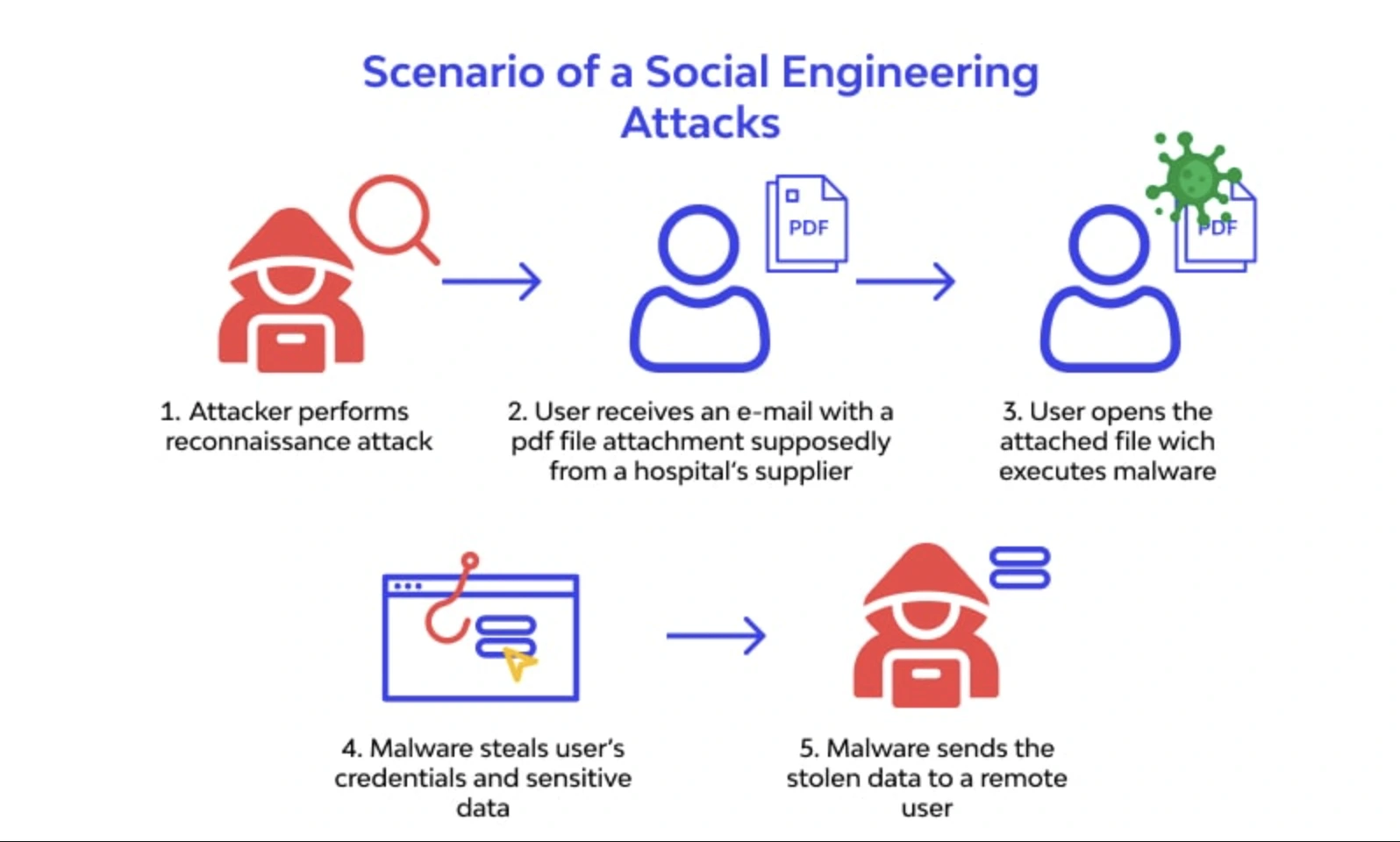
One of the most common methods used by criminals is phishing. Phishing is a type of social engineering attack that uses email or text messages to trick victims into clicking on malicious links or attachments. These links and attachments often contain malware that can steal sensitive information or give hackers access to victims’ systems.
Criminals will also often pose as trusted individuals or organizations in order to gain access to physical locations, systems, or sensitive data. For example, a criminal might call up an employee of a company and pretend to be an IT support representative. The criminal would then ask the employee for their login credentials so that they can “fix a problem.” Once the criminal has the employee’s login credentials, they can gain access to the company’s systems and sensitive data.
Types of social engineering attacks
There are many different types of social engineering attacks. Some of the most common include:
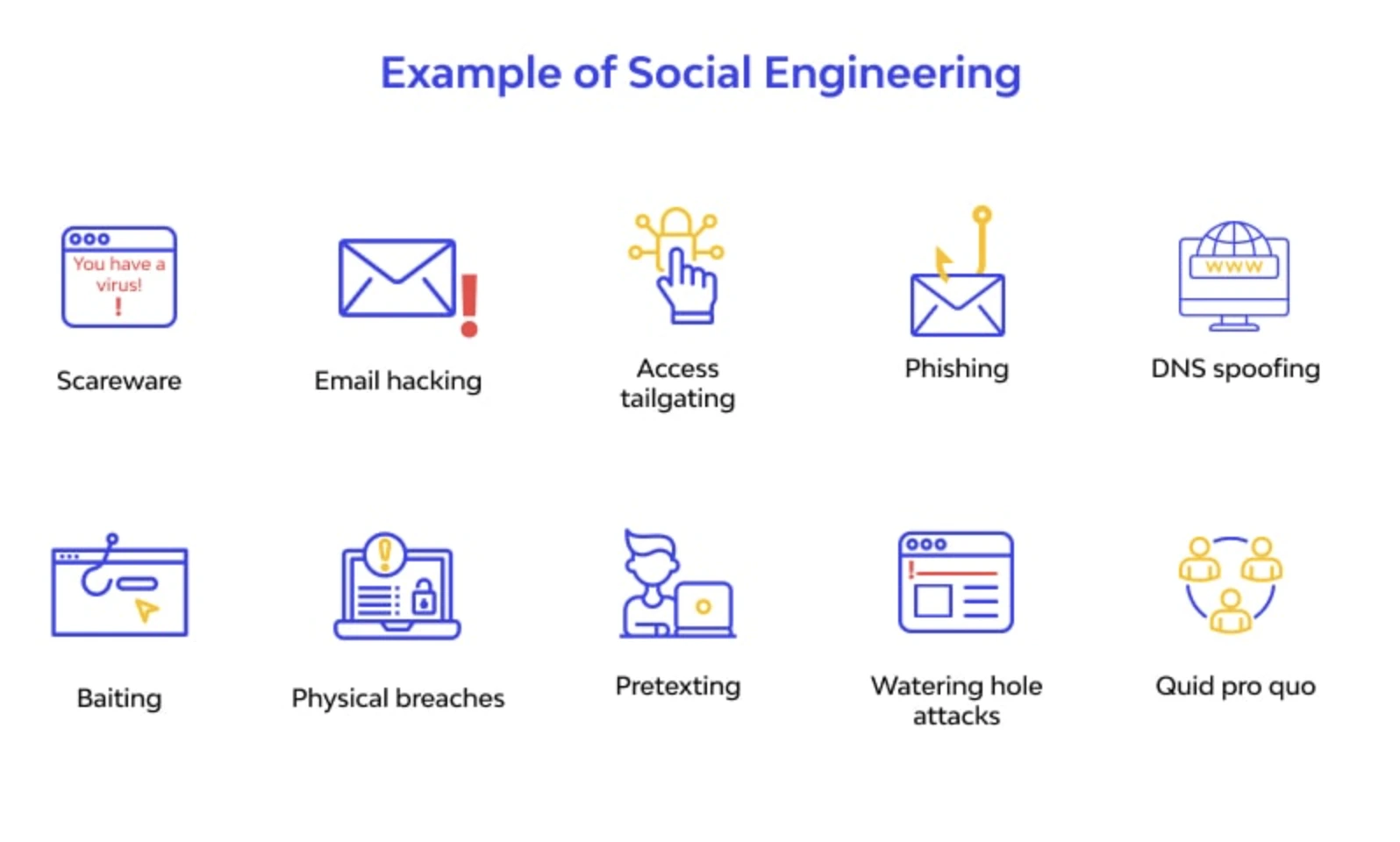
Phishing attacks
As mentioned above, phishing attack is a type of social engineering attack that uses email or text messages to trick victims into clicking on malicious links or attachments.
Baiting attacks
Social engineering baiting attacks are a bit different in that they use physical media (USBs, CDs, etc.) instead of email or text messages. The attacker will leave the physical media in a place where they know the victim will find it (e.g., their desk, car, etc.). The media will usually contain some type of malicious software that, once executed, will give the attacker access to the victim’s system.
Pretexting attacks
Pretexting is a type of social engineering attack in which the attacker creates a false story or scenario in order to obtain sensitive information from the victim.
For example, an attacker might call up a victim and pretend to be their bank. The attacker would then say that there was some suspicious activity on the victim’s account and that they need to verify their information. The victim, not wanting their bank account to be compromised, would then give the attacker their sensitive information.
Quid pro quo attacks
Quid pro quo attacks are a type of social engineering attack in which the attacker offers the victim something in exchange for their sensitive information.
For example, an attacker might call up an employee of a company and say that they’re having problems with their email account. The attacker would then say that they’ll give the employee access to their email account if the employee gives them access to the company’s systems.
Tailgating or piggybacking attacks
Tailgating, also known as piggybacking, is a type of social engineering attack in which the attacker gains access to a physical location by following someone who has legitimate access.
For example, an attacker might tailgate an employee into a building by walking close behind them. Once the attacker is inside the building, they would then have access to all of the sensitive data and systems that are inside.
How can you protect yourself from social engineering attacks?
Now that you have a good understanding of social engineering and the different types of attacks, you’re probably wondering how to protect yourself from these attacks.
The truth is that social engineering attacks can be very difficult to defend against because they often exploit human weaknesses, such as our natural trust in others and our willingness to help. However, there are some things that you can do to protect yourself from these types of attacks.
Ways to recognize social engineering attacks
The first step is to learn how to recognize social engineering attacks. This can be difficult because attackers constantly devise new ways to trick their victims. However, there are some common signs that you can look for:
- You receive an unsolicited email or text message from someone that you don’t know.
- The message contains typos or grammatical errors.
- The message is urgent or contains a sense of urgency.
- The message asks you to click on a link or open an attachment.
- You receive a call from someone that you don’t know.
- The caller is trying to obtain sensitive information from you.
- The caller is trying to get you to download something or click on a link.
Be very careful if you find yourself in a situation where any of the above is true. These are all signs that you might be the target of a social engineering attack.
How to protect yourself from social engineering attacks?
Now that you know how to recognize social engineering attacks, you’re probably wondering how you can prevent them. Unfortunately, there is no surefire way to prevent these attacks. However, there are some things that you can do in order to make yourself a less attractive target:
- Don’t give out personal information to anyone that you don’t know.
- Don’t open email attachments or click on links from people that you don’t know.
- Enable spam filters on your email account and set them to high. Most email providers have this option and will help to filter out some of the phishing emails that you might receive.
- If you receive a call from someone that you don’t know, don’t give out any information. Hang up and call the company back using a number that you know is legitimate.
- Ensure that your computer has a good antivirus program installed and is up to date.
- Use unique and strong passwords (at least eight characters long, with a mix of uppercase and lowercase letters, numbers, and symbols) for all of your online accounts.
- Enable two-factor authentication whenever possible. That way, even if someone gets your password, they won’t be able to access your account without access to your phone.
- Keep your operating system and software up to date.
- Be careful about the information that you share on social media. Make sure you have set your privacy settings.
- If you are an employee of a company, make sure that you know your company’s security policies. Follow them closely.
Another method that you can use to ward off social engineering attacks is to start using a VPN (Virtual Private Network) to encrypt your online traffic and protect your privacy. This creates a secure, private connection between you and the VPN server. This makes it much more difficult for attackers to snoop on your traffic or steal your data.
Of course, not all VPNs are created equal. Some VPNs are much better than others. We recommend using a reputable VPN service like ClearVPN. It’s a fast, secure, easy-to-use VPN service that encrypts your traffic and protects your privacy.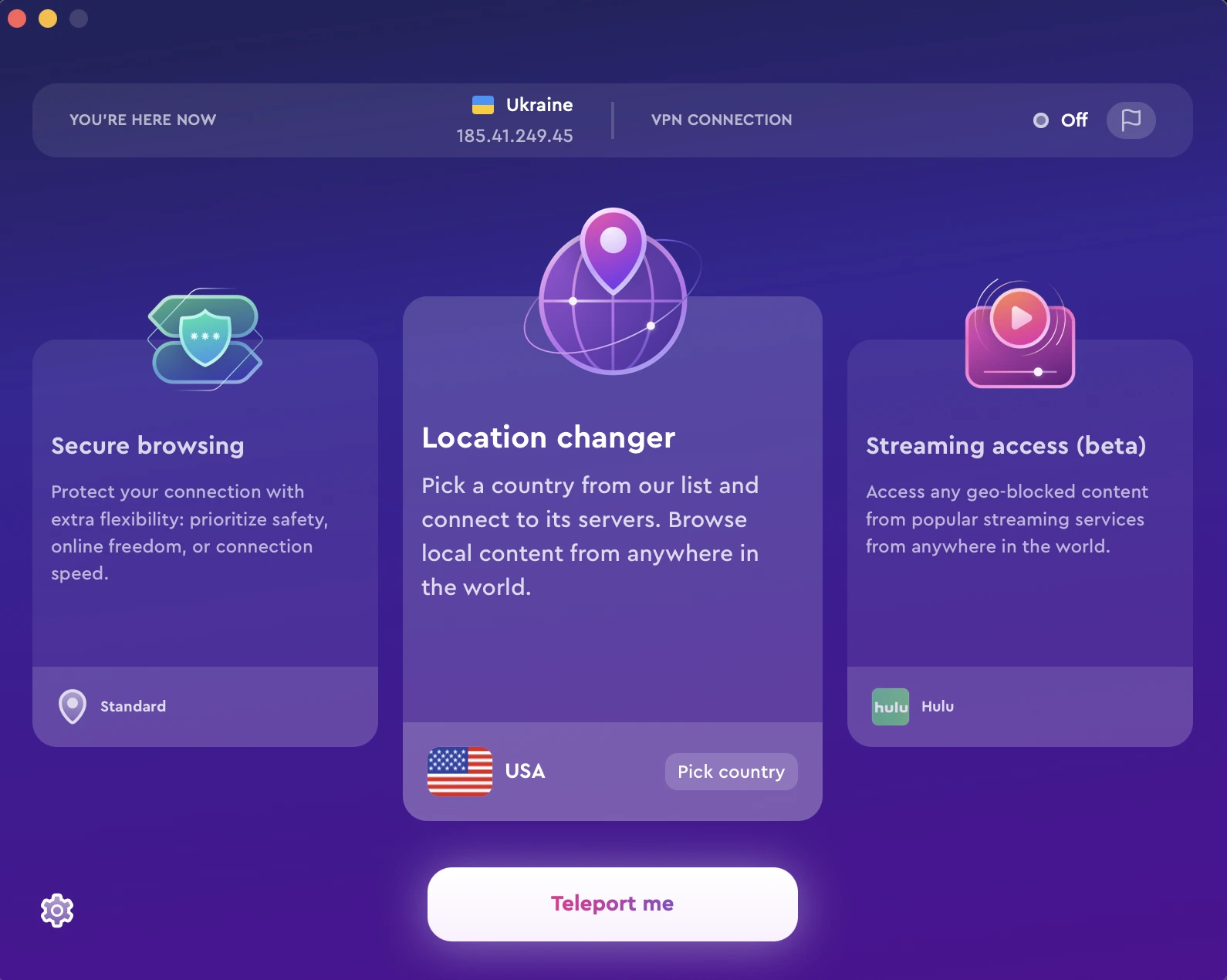
Even if you have not heard of VPNs before or don’t describe yourself as tech-savvy, don’t worry. ClearVPN is very user-friendly and can be set up in just a few minutes. In terms of usage, ClearVPN features shortcut buttons that you can click on depending on what you want to do online, such as “Smart Connection.” It’s that easy!
FAQs
Why do hackers use social engineering?
Hackers use social engineering because it is a very effective way to obtain sensitive information from their victims. By tricking people into giving them this information, hackers can gain access to accounts, steal data, and cause all sorts of mayhem.
What is the best way to prevent social engineering attacks?
There is no surefire way to prevent social engineering attacks, but there are some things that you can do to make yourself a less attractive target. For example, you can enable spam filters on your email account, use strong passwords, and be careful about the information you share on social media.
Can I use a free VPN to protect against social engineering attacks?
If you’re concerned about social engineering attacks, then we would not recommend using a free VPN. This is because free VPNs are often less reliable or secure than paid VPNs. Some free VPNs are actually more dangerous than not using a VPN at all because they sell your data or inject malware into your device.
