Did you know that in 2023, almost 300,000 Americans were phishing victims? And the problem is only getting worse — the study found that phishing attacks increased by a whopping 67% between 2020 and 2022 alone. Phishing is the most common cyber threat, with an estimated 3.4 billion spam emails sent every day worldwide. Given these numbers, it’s clear that we all need to educate ourselves about this threat and learn how to protect ourselves from it.
In this quick guide, we’ll explain what phishing is, how it works, and what you can do to keep yourself safe from these attacks.
What is Phishing?
Phishing – is an online scam where criminals pose as trustworthy entities to trick victims into giving them sensitive information. This information can include login credentials, financial data, or other types of personal information that can be used to commit fraud or steal the victim’s identity.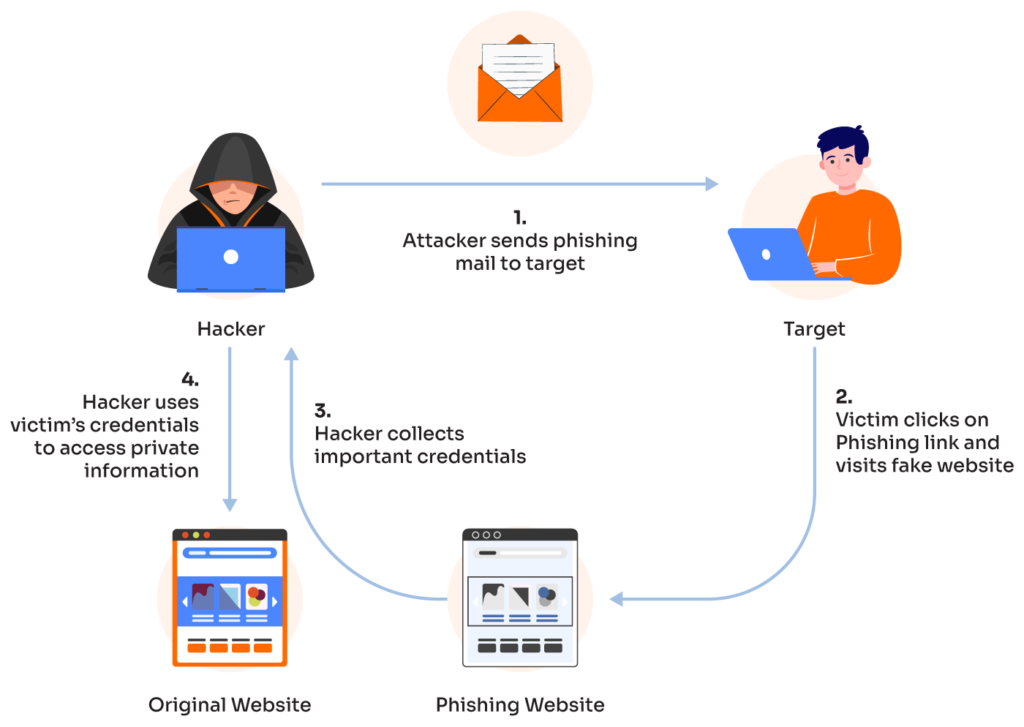
Phishing attacks can take many different forms, but they all have one goal: to trick the victim into giving up their personal information. The attacker may pose as a trusted website, a financial institution, or even a government agency. They will then use this false identity to try and trick the victim into clicking on a malicious link, downloading a malicious attachment, or entering their personal information into a fake website.
How does Phishing work?
A phishing attack usually begins with an email, although it can also come in the form of a text message, instant message, or even a phone call. The attacker will pose as a trusted entity and trick the victim into clicking on a malicious link or attachment. Once the victim clicks on the link or opens the attachment, their device will be infected with malware (malicious software). This malware can then be used to steal the victim’s personal information or commit other types of fraud.
It’s important to note that phishing attacks can happen to anyone, regardless of their level of technical expertise. These attacks are becoming increasingly sophisticated, and even the most tech-savvy individuals can be fooled by a well-crafted phishing email.
Phishing is dangerous because it preys on our natural tendency to trust. We are hardwired to trust the people and institutions we know and recognize, making us vulnerable to these attacks.
What is a common indicator of a phishing attempt?
A common indicator of a phishing attempt is receiving unsolicited emails or messages that urge you to click on a link or download an attachment. These messages often mimic trusted organisations or banks, asking for personal information, such as passwords, credit card details, or social security numbers.
Poor grammar, misspelled words, and generic greetings are also red flags. Additionally, check the sender’s email address, it may look similar to a legitimate one but with subtle differences.
Be cautious of urgent requests or threats in the message, as they aim to create a sense of urgency. Always double-check the legitimacy of such messages and avoid clicking on any suspicious links or sharing sensitive information.
How to protect yourself from a phishing attack
Now that we know what phishing is and how it works, let’s look at some of the best ways to protect yourself from these attacks.
Fortunately, it’s not that difficult to protect yourself from phishing attacks. It all boils down to being aware of the threat and being cautious about the emails, text messages, and phone calls you receive. Following a few simple tips can make it much harder for criminals to steal your personal information.
The first step is to learn to recognize the tell-tale signs of a phishing email. Only then can you take the necessary steps to protect yourself.
How to spot a Phishing email
Phishing can come in many forms, but some common characteristics can help you spot a phishing email. Here are some things to look out for:
- The message is urgent or contains threatening language
- The sender is spoofed or impersonates someone you know or trust
- The message may look like a service you use but the email address might not be 100% correct. For example, instead of [email protected], the email might be [email protected]
- The email contains typos or grammatical errors
- The email contains strange or unexpected attachments
- The email requests personal information or login credentials
If you see any of these red flags, be very suspicious and exercise caution before clicking on any links or opening any attachments. If you’re unsure whether an email is legitimate, the best thing to do is contact the person or company directly to confirm.
Below is a classic example of a phishing email designed to access someone’s Shopify account.
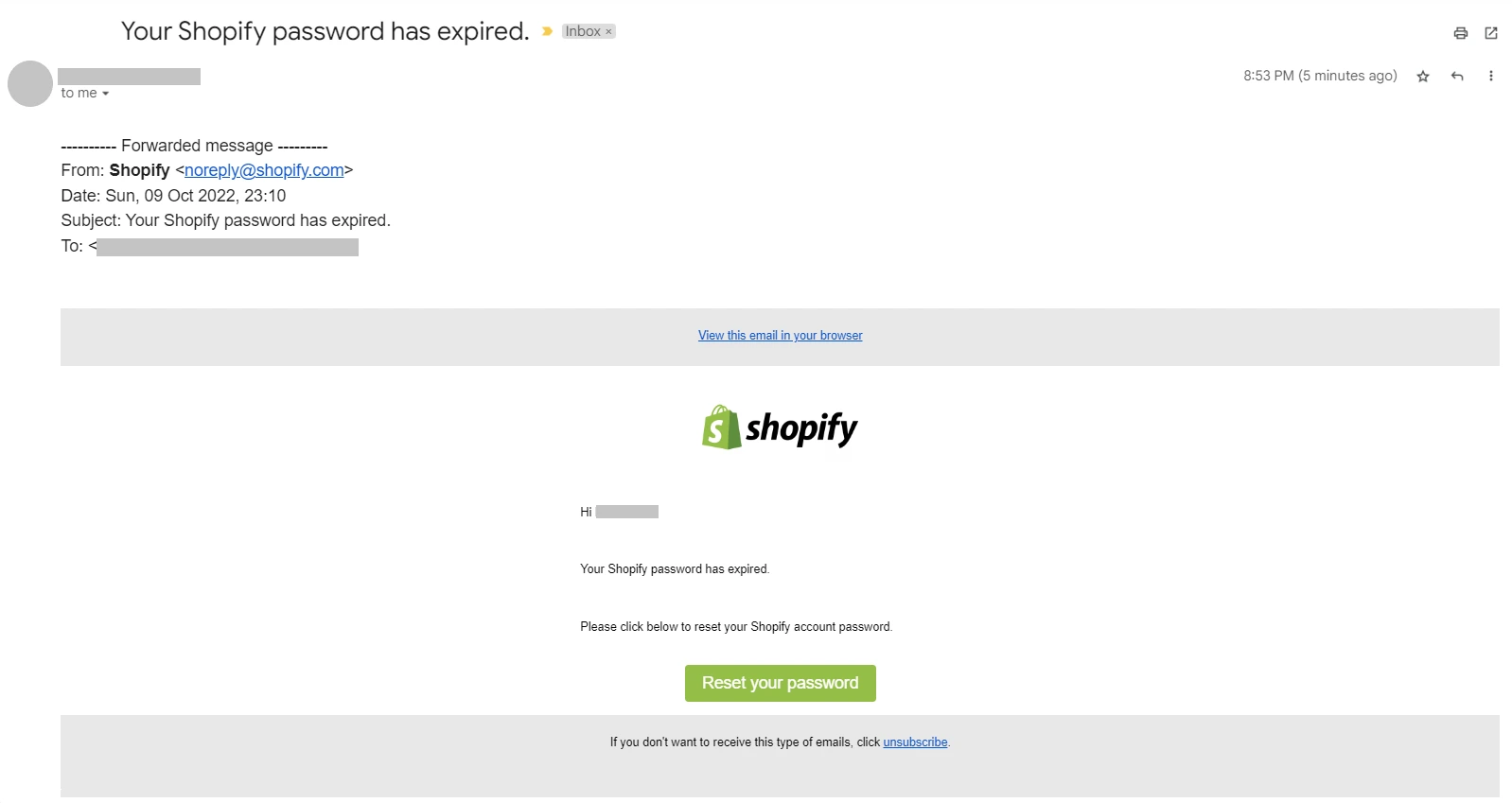
Notice how the sender is disguised to look like Shopify, and how the message uses urgent language to try and trick the victim into clicking on the malicious link. In the email above, the user did not request a password change or anything. This is a very common tactic phishers use, so it’s essential to be aware of it.
Phishing attacks are becoming more and more sophisticated, so it’s important to be vigilant. By being aware of the signs of a phishing email, you can protect yourself and your organization from falling victim to these scams.
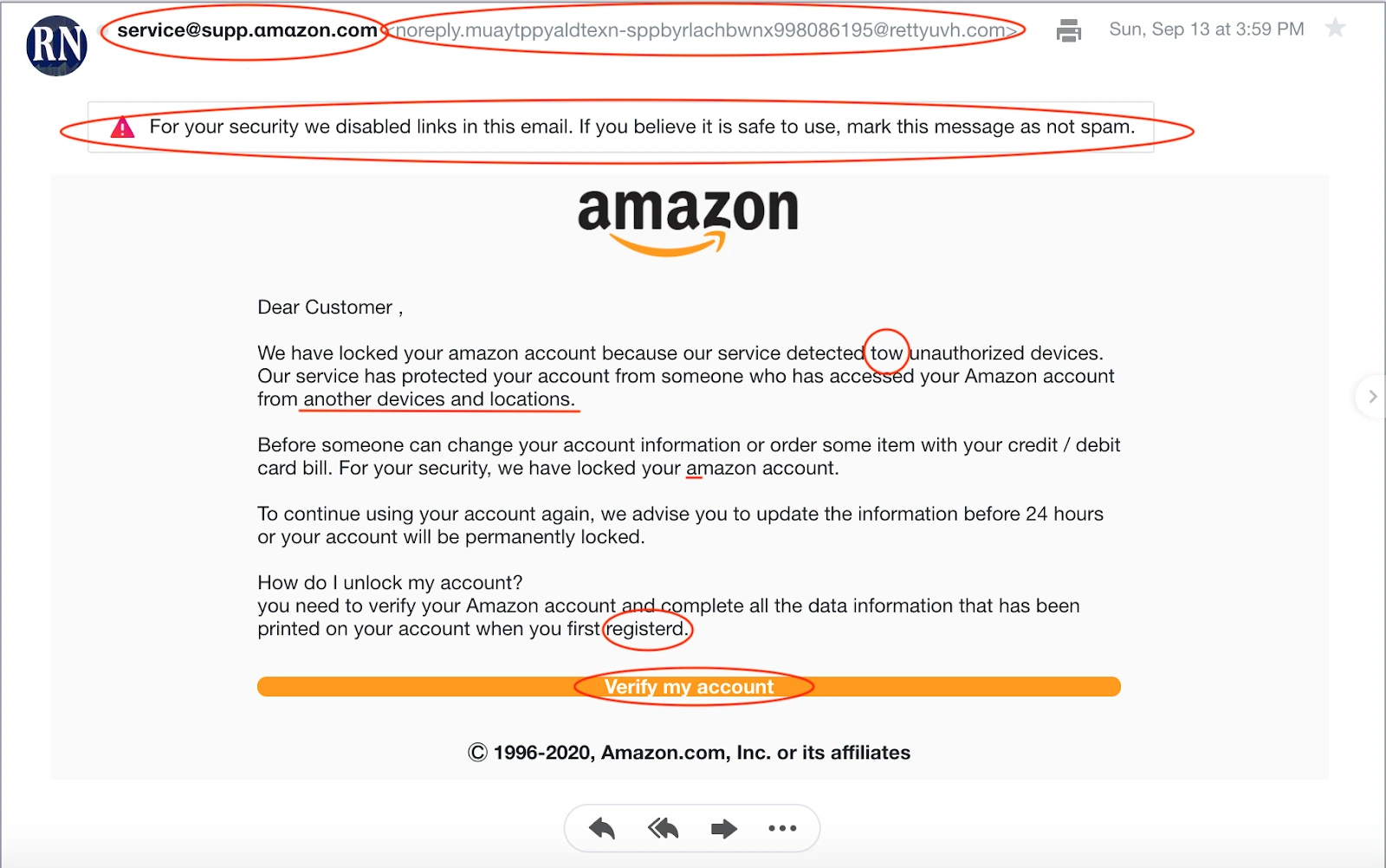
If you think that you’ve been the victim of a phishing attack, it’s important to take action immediately and change your passwords. You should also contact your bank or credit card company to let them know what happened.
But, if you have already clicked on a phishing link, don’t panic, we have a great guide where we have a step-by-step guide on what to do after clicking on a phishing link, check it.
How to avoid phishing attempts that are not via email
Another important thing to remember is that phishing attacks can come in other forms and are not only limited to emails (although that’s the most common). Here are some other ways that phishers can try to get your personal information:
- Text messages: You may receive a text message from what appears to be a trusted sender, but the message contains a link that leads to a fake website. This kind of phishing even has it’s own name, it’s called Smishing.
- Phone calls: You may receive a phone call from someone claiming to be from a trusted organization, such as your bank. They may try to trick you into giving them your personal information or login credentials.
- Instant messages: You may receive an instant message from someone claiming to be a friend or colleague. The message may contain a link that leads to a malicious website.
- Social media messages: Group chats are notorious for passing on suspicious links especially if the members are not aware of phishing attacks. You might be sent a message encouraging you to “enter a draw to win $5000 worth of groceries” from a well-known store.
Just like phishing emails, it’s important to be suspicious of any unsolicited messages you receive. If you’re unsure whether a message is legitimate, the best thing to do is contact the person or company directly to confirm.
How to prevent Phishing
Now that you know what phishing is and how to spot a phishing email, let’s take a look at some of the best ways to prevent these attacks.
1. Set a spam filter on your inbox settings
One of the best things you can do is to use a strong spam filter. This will help to block most phishing emails from reaching your inbox. The process may vary depending on your email provider, but you’ll generally want to look for an option to enable “spam filtering” or “junk mail filtering.”
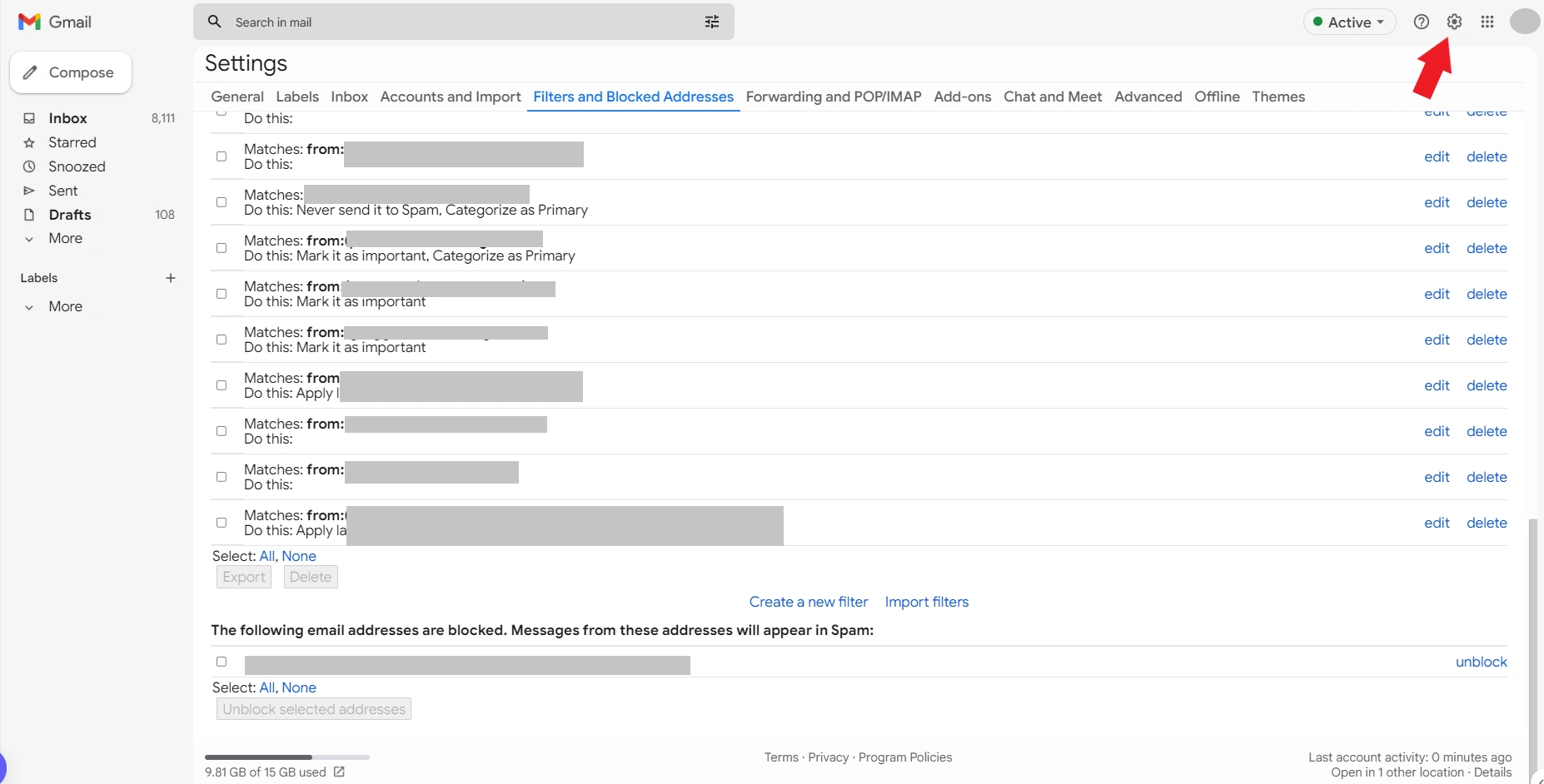
In the case of Gmail (the most popular email service), spam filtering is enabled by default. However, you can further customize your spam filters by going to the “Settings” menu and selecting the “Filters and Blocked Addresses” option. You can add specific words or phrases you want to block from here.
2. Enable two-factor authentication
You should also make sure to enable two-factor authentication (also known as two-step verification) whenever possible. This adds an extra layer of security by requiring you to enter a code sent to your phone and your password when logging into an account.
Most major online services like Google, Facebook, and Twitter offer two-factor authentication. To enable it, you’ll usually need to go to the “Security” or “Settings” menu and look for an option to enable two-factor authentication.
3. Encrypt your info by using a VPN
Another good way to prevent phishing attacks is to encrypt your internet traffic so hackers can’t intercept your personal information. You can do this with ClearVPN, which encrypts your traffic and routes it through a secure server. That way, even if you do click on a malicious link, your personal information will be protected.
To use ClearVPN, simply download ClearVPN and connect to one of our secure servers. We have servers in over 45 countries, so you can always find one close to you for the best connection speeds.
Lastly, one of the best ways to protect yourself from phishing attacks is to educate yourself and others about these threats. The more people are aware of phishing scams, the harder it will be for attackers to succeed.
FAQs
What makes phishing so deceiving and dangerous?
Phishing is deceiving and dangerous because it cleverly disguises as trusted entities, like banks or reputable companies, making it challenging to spot. It preys on human psychology by creating a sense of urgency or curiosity, urging victims to click on malicious links or share personal information.
Phishers continually evolve their tactics, using social engineering techniques to exploit vulnerabilities. Once they succeed, they can steal sensitive data, compromise accounts, or spread malware.
How not to be a victim of phishing?
To avoid falling victim to phishing:
- Be cautious of unsolicited emails or messages;
- Always double-check sender addresses;
- Watch for grammatical errors, and avoid clicking on suspicious links;
- Never share personal or financial information through unsolicited channels.
- Use strong, unique passwords and enable two-factor authentication for added security.
