In 2021, cybercrime cases rose as cybercriminals took advantage of the new norm — the work-at-home culture and digital transformation caused by the global pandemic. The most widely-reported attacks were data breaches and phishing. Both of these cyber crimes can be prevented with diligent cyber hygiene practices.
In this guide, we’ll cover good cybersecurity practices to ensure a safer online environment for you and your loved ones.
What is Cyber Hygiene?
Cyber hygiene describes a set of routine practices that help you secure your computer, mobile phones, and other internet-connected devices against unauthorized access.
Just like personal hygiene practices can keep sickness at bay, cyber security hygiene practices are the basics that help prevent your devices from being infected by unknown agents.
Like washing and sanitizing your hands has become the norm for us, it’s important to make good cyber hygiene practices a regular habit in all situations. For example, use strong, non-repetitive passwords for all websites, whether you’re transferring money or reading manga online. Always use two-factor authentication for your emails and accounts.
It takes consistency and discipline to maintain a high level of protection and reduce vulnerabilities that cybercriminals can manipulate.
Top 10 Cyber Hygiene Tips
Follow these 10 steps to improve your cyber security and build the habit of good cyber hygiene practices.
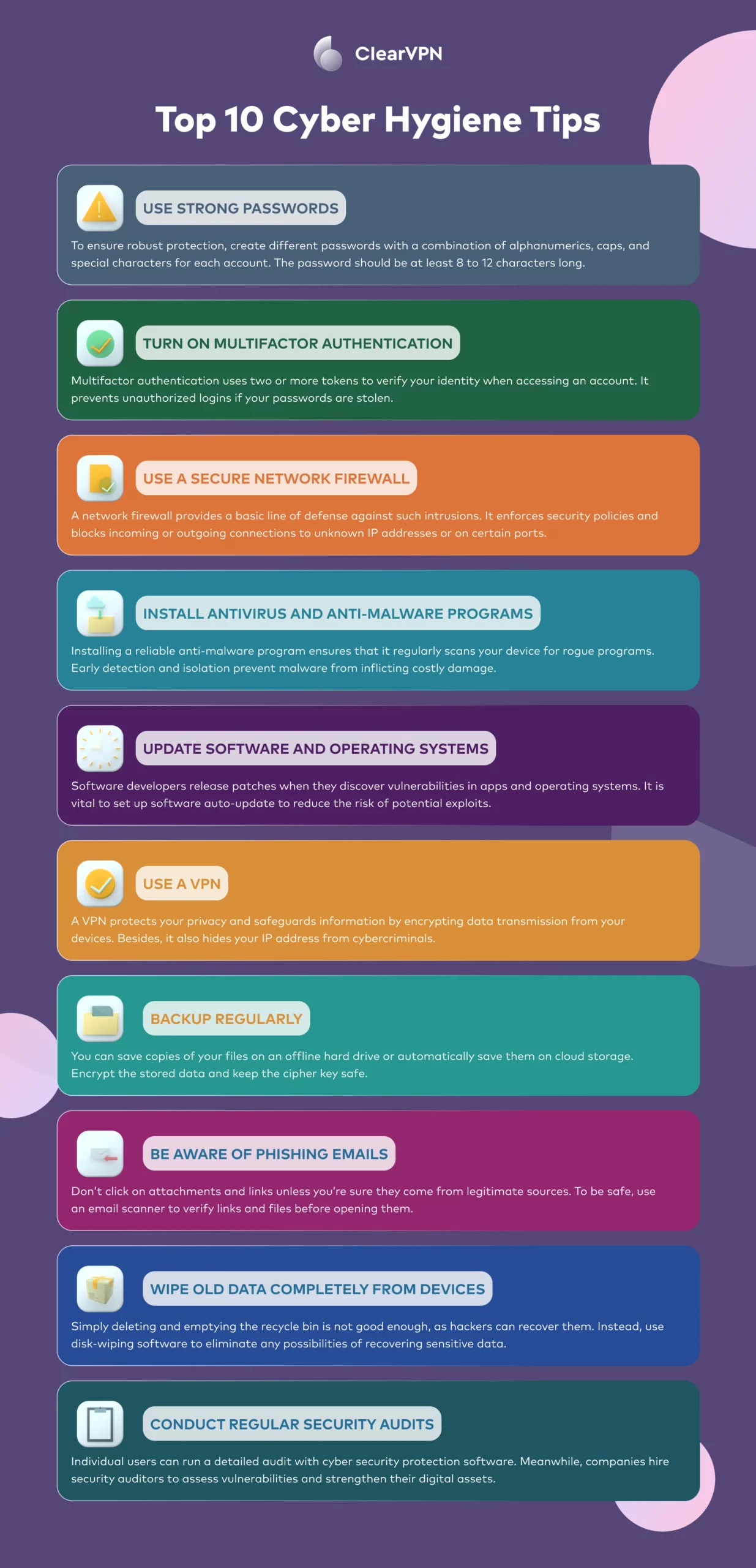
1 – Use strong passwords
People tend to stick with simple, easy-to-remember passwords as they manage access to dozens of accounts. However, using passwords like birth dates or ‘admin’ is a recipe for disaster. Cybercriminals can easily brute-force their way into the account if you use weak passwords, and the attack will be even more devastating if you use the same password for all accounts.
To ensure robust protection, create different passwords with a combination of alphanumerics, caps, and special characters for each account. Make sure that the password is at least 8 to 12 characters long. Use a password manager if you need help remembering all the passwords. Here you will find a detailed guide on how to create a strong password for all your accounts.
2 – Turn on 2FA or Multifactor Authentication
Multifactor authentication uses two or more tokens to verify your identity when accessing an account. It prevents unauthorized logins if your passwords are stolen. For example, your banking app sends an OTP code to your mobile phone and requires you to manually key it on the app before granting access. Some software supports biometric identifications, which makes it harder for cybercriminals to force their way in.
3 – Use a secure network firewall
Some hackers launch targeted attacks to steal information or disrupt computer services. A network firewall provides a basic line of defense against such intrusions. It enforces security policies and blocks incoming or outgoing connections to unknown IP addresses or on certain ports. You will need a network server to protect servers and databases against possible breaches.
4 – Install antivirus and anti-malware programs
Using a device without adequate virus and malware protection is poor cyber hygiene practice. In 2021, 5.4 billion malware attacks were recorded, and the number shows that many of us are at risk without antivirus and anti-malware programs. Malware infection might lead to severe consequences, such as data loss, hardware damage, and identity theft.
Thankfully, many devices are pre-installed with reliable anti-malware programs. Turning it on or installing a reliable anti-malware program ensures that it regularly scans your device for rogue programs that you unknowingly downloaded. Early detection and isolation prevent malware from inflicting costly damage and spreading to other devices on the network.

5 – Update software and operating systems
Software and operating systems might contain vulnerabilities that hackers can exploit. For example, the infamous WannaCry ransomware targeted a known vulnerability in the Microsoft Windows system and infected hundreds of thousands of computers in days. Many of these attacks could have been avoided if the users had updated their software and operating system with the security fix.
Software developers release patches when they discover vulnerabilities in apps and operating systems. Considering the large number of apps installed by the average user, it is vital to set up software auto-update to reduce the risk of potential exploits.
6 – Use a VPN
You don’t know who’s spying when you’re browsing the internet, particularly on an unprotected public WiFi connection. It is risky to run banking transactions or share confidential information without a VPN. A VPN protects your privacy and safeguards information by encrypting data transmission from your devices. Besides, it also hides your IP address from cybercriminals.
I use ClearVPN to add a layer of stealth and security when browsing the internet. ClearVPN uses secure VPN protocol and military-grade encryption to reduce cybersecurity vulnerabilities. Moreover, experts at Forbes like how ClearVPN helps to solve data security concerns with its proprietary technologies.
Want to try the ClearVPN app, just follow these 3 simple steps:
- Go to the ClearVPN website and download the app for your device.
- Create your account.
- Run the app and enjoy!
7 – Backup regularly
Back up important files regularly so you don’t end up being locked out of your work device. You can save copies of your files on an offline hard drive or automatically save them on cloud storage. Encrypt the stored data and keep the cipher key safe. If your device is compromised, you can recover from the saved data and ensure minimum disruption to your work.
8 – Be aware of phishing emails
Cybercriminals have upped their game when tricking users into divulging sensitive information. They use phishing emails, a social engineering attack, to lull users into complacency. These days, phishing emails take the form of seemingly legit emails from an acquaintance or co-worker. This makes spotting and avoiding phishing attacks much more difficult.
Therefore, one critical cyber security hygiene practice is to remain alert when opening emails. Don’t click on attachments and links unless you’re sure they come from legitimate sources. To be safe, use an email scanner to verify links and files before opening them.
9 – Wipe old data completely from devices
If you use company laptops or plan to sell off your personal computer or device, it’s prudent to remove all your personal data from the devices. Simply deleting and emptying the recycle bin is not good enough, as hackers can recover them if they get hold of the computers. Instead, use disk-wiping software to reformat the devices and eliminate any possibilities of recovering sensitive data.
10 – Conduct regular security audits
The cybersecurity landscape constantly changes and requires an equivalent response to emerging threats and vulnerabilities. You cannot rely on old cybersecurity practices to counter new forms of cyber attacks. Therefore, running a thorough security audit is essential to learn how exposed you are to external threats and create appropriate cyber defense plans.
Individual users can run a detailed audit with cyber security protection software. Meanwhile, companies hire security auditors to assess vulnerabilities and strengthen their digital assets.
Your actionable cyber hygiene checklist
Here’s a summary of cyber hygiene best practices to help you increase digital resilience against growing threats.
✅ Passwords — Avoid using the same password for different accounts. Use strong passwords that are impossible to guess.
✅ Multifactor authentication — Enable multifactor authentication for critical accounts.
✅ Secure your network firewall — Use network firewalls to filter and block suspicious connections.
✅ Anti-malware and antivirus programs — Scan your devices with anti-malware and antivirus programs. Update anti-malware and antivirus programs to protect against the latest threats.
✅ Update operating systems and apps — Enable auto-update for operating systems and apps to prevent vulnerability exploits.
✅ Get a reliable VPN — Connect to a VPN at all times to ensure online privacy.
✅ Backup your files — Automatically back up sensitive files to the cloud or offline storage.
✅ Delete suspicious emails or messages — Do not click on suspicious emails, links, and attachments.
✅ Completely remove all data from old devices — Wipe all unused and sensitive data clean on shared devices.
✅ Stay on top of your cyber security — Regularly assess your cyber defense readiness,
FAQs
Why are cyber hygiene best practices important?
The growing number of cyber-attacks means you must be vigilant when using the internet. It’s a mistake to assume that cybercriminals will never target you. Instead, taking proactive actions and cultivating good cyber security habits are the best ways to protect yourself against known and unknown threats.
How can we avoid online threats?
Online threats appear in different forms, and some can go undetected for a long period. A robust cyber security protection strategy involves thorough vulnerability assessments and mitigation plans. It starts with good cyber hygiene habits.
How to implement cyber hygiene for employees?
As employees adopt the new working culture, they become vulnerable to cyber-attacks. Therefore, organizations must ensure that they train employees with good security habits and elevate their awareness. Using security tools, such as antivirus and VPN, on workplace devices also help employees to prevent data breaches and safeguard company assets.
