No one can deny that privacy and security are major concerns in the digital age. Cyber threats are ever-evolving; some have become so sophisticated that they can monitor and record our online activities in secret. This highlights the need to seriously consider solutions to protect our personal information — which is exactly where VPN protocols come in!
In this quick guide, we’ll explore the ins and outs of VPN (Virtual Private Network) protocols, their various types, and how they compare. Only then May one appreciate the value that each VPN offers and determine the best fit for your privacy needs.
Let’s dive in!
What is a VPN protocol?
First things first — what exactly do we mean by VPN protocol? After all, understanding this is essential before we delve into the various types and how they work.
In simplest terms, a VPN protocol refers to rules that determine how information is shared between a user’s device and a VPN server. These rules determine how to encrypt and secure your data as it travels through the Internet.
Various VPN protocols have been created as privacy needs and threats have evolved. These differ in terms of speed, security, and overall performance. This means that one protocol can be a perfect choice in certain situations, and close to useless in others. That’s why it’s essential to understand the different types of VPN protocols and their defining features before deciding which one to use.
Types of VPN protocols
Now that we understand what VPN protocols are for, let’s move on to explore some of the most popular types out there. Note that while this is not an exhaustive list, these protocols represent many of the most common options that users will typically come across.
As you’ll later learn, each protocol has its own defining features and characteristics that users should consider before leveraging them as a potential security solution.
Here is a short overview of some of the most common types of VPN protocols used today:
PPTP: the fastest VPN protocol
Regarding speed, nothing beats the good old PPTP (Point-to-Point Tunneling Protocol), first introduced in the 1990s. As one of the oldest protocols in existence, it’s fairly easy to set up and fast due to minimal encryption measures.
Unfortunately, this also means that it’s not as secure as other VPN protocols, so it’s not ideal in cases that require high levels of privacy and security measures. For example, PPTP might be suitable for bypassing geo-restrictions, but not for torrenting, online banking, etc.
L2TP/IPsec: best support & compatibility
L2TP (Layer 2 Tunneling Protocol) is an improved version of PPTP and is often implemented in combination with IPsec (Internet Protocol Security). While not as fast as PPTP, this VPN protocol offers stronger encryption as well as compatibility with most operating systems.
IKEv2: a fast & stable VPN protocol for mobile devices
As mobile devices became more common, the VPN industry saw a need for a new VPN protocol that’s light (requires less computing power) yet stable enough to be used on portable devices like smartphones and tablet computers.
IKEv2 stands for “Internet Key Exchange Version 2” and one of its key advantages is the ability to quickly switch between mobile and Wi-Fi networks.
OpenVPN: the most secure VPN protocol
Data security experts widely consider OpenVPN as the best VPN protocol and for good reason. For one thing, it uses a technique called SSL/TLS encryption (Secure Sockets Layer & Transport Layer Security) for key-hashing authentication. This prevents any alterations to the data as it’s transmitted over the Internet.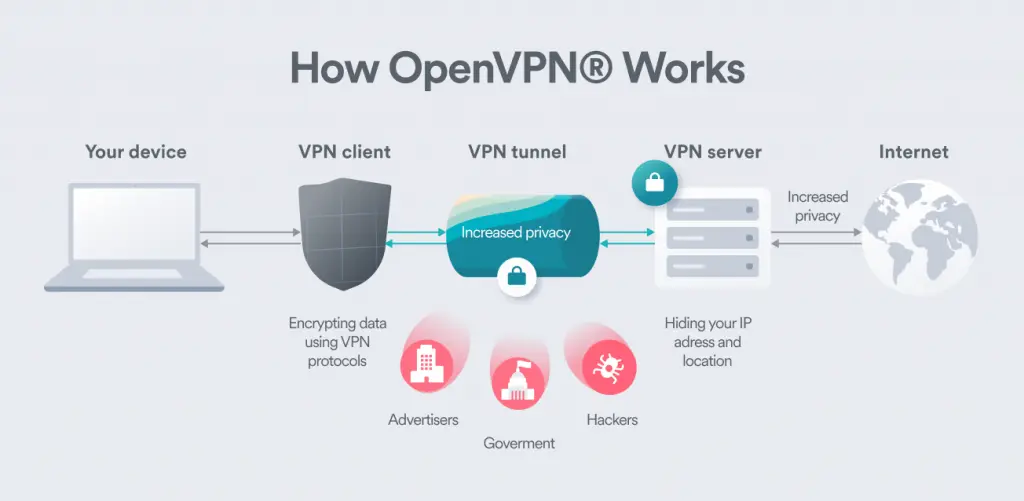
Another notable advantage of OpenVPN is that it’s open source. This means that developers and security experts can easily access its code and make improvements as vulnerabilities arise. As a result, OpenVPN has evolved into one of the most secure and reliable VPN protocols available today.
VPN protocols comparison
If you’re new to VPNs, then you’ll find that most service providers offer a combination of the VPN protocols mentioned above. Therefore, it might be helpful to see how these protocols compare with one another.
Here’s what you can expect out of these VPN protocols:
- Security: OpenVPN and IKEv2 are considered the most secure VPN protocols, while PPTP is the least safe due to its known vulnerabilities.
- Speed: PPTP is typically the fastest VPN protocol, followed by IKEv2 and OpenVPN. L2TP/IPsec may be slower due to its double encapsulation process.
- Compatibility: OpenVPN and L2TP/IPsec are widely supported across various platforms, whereas IKEv2 may not be available on all devices.
- Ease of use: PPTP and L2TP/IPsec are generally easiest to set up, while OpenVPN may require the most configuration.
Choosing the best VPN Protocol
As you may have already realised, there’s not one definitive answer to which protocol is the best. This is because the answer ultimately depends on your needs.
For instance, if your primary concern is privacy, then you cannot go wrong with OpenVPN or IKEv2. But if you’re more concerned about speed and how using a VPN might affect your browsing experience, then PPTP may be enough,as long as you’re aware of its limitations.
ClearVPN: A VPN solution with automatic protocol selection
Unsure as to what VPN service to use? You may want to consider ClearVPN — a reliable and user-friendly Fast VPN service that automatically switches between multiple VPN protocols based on usage requirements. This includes IPSec & IKEv2 for fast connections and the tried-and-true OpenVPN protocol.
With these options, ClearVPN can quickly adapt and leverage the most suitable VPN protocol based on your specific need, whether bypassing geo-restrictions, masking your IP address, using VPN for streaming, etc.
You can download and try ClearVPN 2 for free here. ClearVPN offers a free 3-day trial and it is the same as a full version of the app. Start your free trial here.
FAQs
Which VPN protocol is best?
The best VPN protocol for you depends on your specific needs and priorities. OpenVPN is often considered the best overall choice due to its robust security features, speed, and widespread support. However, IKEv2 may be a better option if you’re using a mobile device and require a fast, stable connection.
What type of VPN is most commonly used today?
OpenVPN is today’s most commonly used protocol due to its strong security features, speed, and compatibility with various platforms.
Which VPN protocol is the most secure?
When it comes to security, OpenVPN stands out as one of the most reliable options. It is known for its robust encryption standards, OpenVPN utilises the OpenSSL library and supports a wide range of cryptographic algorithms. This makes it highly configurable, striking an excellent balance between security and performance.
