In 1992, when the first sms was sent from a computer to a mobile phone, it revolutionized the industry. Along with that came scams such as: “You’ve just won the Lotto, please call this number 12345 to claim your prize…” Of course, most of us knew these were scams, especially if we hadn’t played the Lotto or weren’t related to a royal prince from Africa.
Based on statistics from Earthweb site, on average, Americans receive nearly 40 spam text and messages per person per month. Smishing attacks have increased by over 700% in the first half of 2022, compared to a previous year.
However, nowadays, sms scams also known as smishing attack are far more sophisticated and difficult to spot. How’s how to identify and protect yourself and your loved ones from these attacks.
What is Smishing?
Smishing is a form of phishing attack that uses SMS text messages to send malicious links to unsuspecting victims. The goal of this type of attack is to get the recipient to click on the link, which can lead them to a spoofed website or an infected app. The attacker will then try to gain access to sensitive information such as passwords, credit card numbers, and other personal data.
Here’s an example of a smishing attack that targeted bank users:
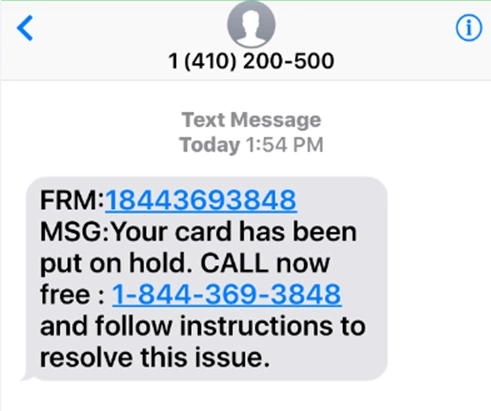
Smishing has become increasingly popular over the past few years with cybercriminals as they can be more difficult for individuals to recognize than traditional phishing attacks. This is due in part to the fact that many people are accustomed to receiving text messages and may not think twice before clicking on a link.
How does Smishing work?
Smishing attacks rely on social engineering tactics (aka playing on your fears) to fool victims into taking unwanted actions. The attackers will typically craft messages that appear to be from a legitimate source, such as a bank or credit card company, in order to gain the victim’s trust.
Once they have gained the individual’s trust, they will then send a link or attachment in the text message that will direct them to a spoofed website or an infected app. Once the victim clicks on the link, they may be prompted to enter personal information such as passwords, credit card numbers, and other sensitive data which can then be used by the attacker to gain access to accounts or financial resources.
For example, a smishing attack may target a victim by appearing to be an alert from their bank, telling them that there is suspicious activity on their account and asking them to click on a link in order to verify their identity. The link then leads the individual to a fake website where they are asked for personal information such as passwords or credit card numbers — which are then stolen by the attacker.
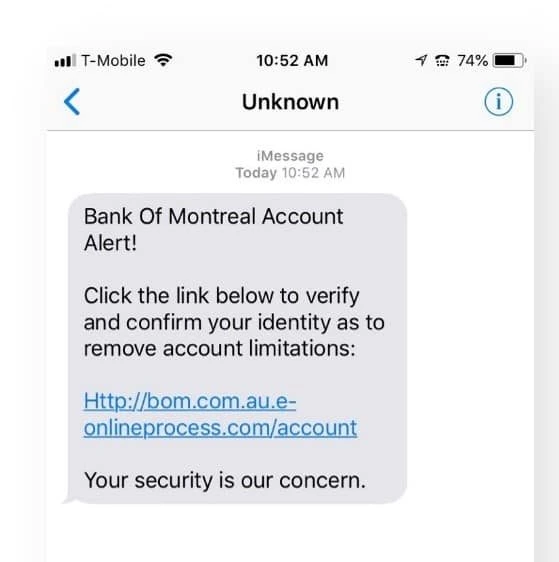
Smishing vs Phishing
If you’re familiar with phishing, then it may sound awfully similar to smishing. But there are a few key differences between these two forms of attack:
- Phishing attacks are typically delivered through email while smishing attacks are sent via text message.
- Phishing messages may appear more suspicious due to the fact that they often contain misspellings or bad grammar — whereas smishing messages are often crafted to look more legitimate.
- Smishing messages are generally sent in bulk and can be difficult for individuals to recognize, as they may appear to come from a source that the recipient trusts.
How to prevent Smishing?
The best way to protect yourself from smishing attacks is to remain vigilant and be aware of any unsolicited messages that you receive. Here are some tips on how to do so:
- Always verify the source before clicking on any links or attachments in a text message. If the message appears suspicious, contact the organization directly through its official website or contact number to verify the legitimacy of the message.
- Be wary of messages that ask for personal information or financial data. Legitimate organizations will never request this kind of information via text.
- Enable two-factor authentication on your accounts whenever possible, as this can help protect your data in case an attacker is able to access it.
- Install an anti-malware program on all of your devices as this can help to protect them from malicious software and detect suspicious activity.
- Be sure to update your device’s operating system regularly, as this can help to keep it secure against the latest security threats.
Finally, it’s important to report any phishing or smishing attacks that you encounter as soon as possible. By doing so, you can help to protect yourself and others from becoming victims of cybercrime. With the right precautions and awareness, you can stay one step ahead of cybercriminals and keep your data secure.
Protect against Smishing attacks with a VPN
Another way to protect yourself from smishing attacks is to start encrypting your internet connection so that any messages you send and receive are protected from hackers and identity thieves. You can do that with a premium VPN service like ClearVPN.
With ClearVPN, you can protect your data with military-grade encryption and keep your device safe from malicious software. Plus, its Smart Rules feature allows you to customize and save security settings so that all of your online activities remain secure and anonymous. 
ClearVPN app works on all major platforms, including Windows, Mac, iOS and Android. So no matter what device you use for your online activities, you can rest assured that your data is safe and secure.
FAQs
What happens if you click on a smishing text?
If you click on a link contained in a smishing text, you may be taken to a malicious website where your personal information can be stolen. To protect yourself, always verify the source of any unsolicited messages before clicking on any links or attachments.
Can you stop smishing?
Yes! The best way to prevent smishing attacks is to remain vigilant and be aware of any unsolicited messages that you receive. Make sure to verify the source of a message before clicking on any links or attachments, and always use two-factor authentication whenever possible.
Additionally, it’s important to have an up-to-date anti-malware program on all of your devices and use a VPN service like ClearVPN to encrypt your internet connection and protect your data from cybercriminals.
Should you report smishing attempts?
Yes, it’s important to report any phishing or smishing attempts as soon as possible. By doing so, you can help to protect yourself and others from becoming victims of cybercrime. Additionally, you can alert authorities so that they’re aware of the threat and can take the necessary steps to prevent future attacks.
You should also report any suspicious activity on your accounts to your bank or credit card provider as soon as possible. This will help them to identify any potential fraud and take the necessary steps to protect your data.
