Did you know that in 2023, there were over 317 million ransomware attacks worldwide? The United States maintains its leading position, accounting for approximately 50% of all ransomware attacks. In the world of cyberattacks, ransomware is one of the worst kinds of malware out there. It can lock you out of your computer, encrypt your files so you can’t access them, and even hold your computer hostage until you pay a ransom. While ransomware has been around for a while, it’s recently been on the rise — costing businesses and individuals millions of dollars.
In this article, we’ll explain what is ransomware, how to protect yourself against it, and what to do if you’re infected.
What is Ransomware?
As the name implies, ransomware is a type of malware designed to hold your computer or data, hostage, until you pay a ransom. It typically comes in the form of an email attachment or a malicious website that will download and install the ransomware on your computer without you even knowing it.
Once installed, ransomware can encrypt your files, making them inaccessible, or it can lock you out of your computer entirely. In some cases, ransomware will also delete your backups, so you can’t recover your data.

As you might imagine, this form of cyberattack is a serious threat to businesses and individuals alike. From a financial side, it’s predicted that by 2031, the annual cost of ransomware will be about USD$265 billion. Not only can it cause massive financial damage, but it can also disrupt your operations. In some cases, it can even lead to data loss.
Fortunately, there are steps you can take to protect yourself from ransomware. But before we get to that, it’s important to get a good grasp of how this malware works.
How does ransomware work?
Once ransomware finds its way into your device, it will start to encrypt your files with a strong encryption algorithm. After the encryption process is completed, the ransomware will display a ransom note on your screen, demanding you to pay a certain amount of money (usually in bitcoins) to decrypt and regain access to your files.
In some cases, the attackers also threaten to delete or release the encrypted files if the ransom is not paid within a certain time frame. Any attempt to remove the ransomware from your device without paying the ransom will result in the encrypted files being permanently lost.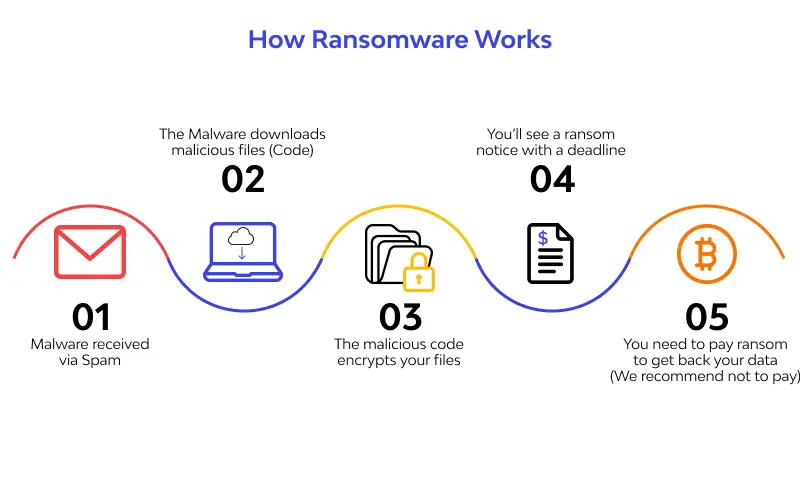
With that said, simply paying the ransom does not guarantee that you will get your files back. The majority of the time, victims who pay the ransom never end up receiving the decryption key from the attackers.
And it’s not just PC or Windows users who have reason to worry. Today’s ransomware can infect just about any internet-capable device, including Macs, iPhones, Android smartphones, and even smart TVs.
Types of ransomware
Now that you have a good grasp of how ransomware works, let’s take a look at some of the most common types of ransomware. There are various types depending on how they spread and infect a device.
- Phishing — This is a common type of social engineering attack in which the attacker sends an email that appears to be from a legitimate source, such as a bank or service provider. The email will contain a link or attachment that, when clicked, will download and install the ransomware on your device.
- Exploit kits — These are tools that attackers use to exploit vulnerabilities in software in order to infect a device with ransomware. Once a vulnerability is found, an attacker can create an exploit and add it to an exploit kit. These kits are then used to infect devices connected to the same network that have the same vulnerability.
- Malvertising — This is a type of attack in which the attacker uses advertising networks to display malicious ads on legitimate websites. When you click on one of these ads, you will be redirected to a malicious website that will download and install the ransomware on your device.
- Drive-by downloads — This is a type of attack in which the attacker uses a malicious website or ad to download and install the ransomware on your device without you even knowing it.
Keep in mind that a ransomware attack may not start immediately after a device is infected. In some cases, the attacker will wait for some time before encrypting the files or displaying the ransom note. This is done to avoid detection and increase the chances that the victim will pay the ransom.
What are some of the most notable examples of ransomware attacks?
Perhaps the most infamous type of ransomware is WannaCry, which was responsible for infecting more than 230,000 computers in over 150 countries in 2017. The attackers behind WannaCry used a vulnerability in the Windows operating system to spread the malware and encrypt victims’ files.
Another well-known type of ransomware is Cryptolocker, which first appeared in 2013. Cryptolocker was notable for being the first type of ransomware to use asymmetric encryption, which made it much more difficult to decrypt the files without paying the ransom.
More recently, in 2020, a new type of ransomware called Maze began appearing. Maze is unique in that it not only encrypts victims’ files but also steals and exfiltrates them. The attackers then threaten to release the stolen data if the ransom is not paid.
These are but a few examples of the many types of ransomware that have been used in attacks. Collectively, they’re responsible for causing billions of dollars in damage and affecting millions of people around the world. When you consider just how much harm ransomware can cause, it’s no wonder that it’s become one of the most feared cyber threats.
So this begs the question — what can you do to protect yourself from these cyberattacks? While there’s no guaranteed way to prevent all ransomware infections, there are some steps you can take to reduce your risk.
How to protect against Ransomware
Phishing attacks are one of the most common ways that ransomware is spread. Fortunately, there are steps you can take to protect yourself from these types of attacks.
Best thing you can do is to be cautious when opening email attachments or clicking on links in emails, even if they appear to be from a legitimate source. If you’re not expecting an email with an attachment, be sure to contact the sender to confirm that they actually sent it before opening it.
It’s also a good idea to avoid clicking on links in emails from people you don’t know. If you do receive an email from someone you don’t know and it contains a link, do not click on it. Instead, go to the website directly by typing the URL into your browser.
Another good way to protect yourself from phishing attacks is to use an anti-phishing tool. This is software that can help to identify and block phishing emails. Many email providers, such as Gmail and Outlook, already have built-in anti-phishing protection.
How to protect from ransomware exploit kits?
The scary thing about exploit kits is that they can be used to exploit vulnerabilities in just about any type of software. This means that just about any internet-capable device is at risk of being infected with ransomware.
Fortunately, there are steps you can take to protect yourself from these types of attacks. One of the best things you can do is keep all of your software up to date. When a new vulnerability is found, software developers will release a patch to fix it. By keeping your software up to date, you can help to ensure that any new vulnerabilities are patched and that your device is protected.
How to prevent ransomware malvertising attacks
Malvertising is a type of attack that can be difficult to protect yourself from. This is because malicious ads can appear on legitimate websites, making them difficult to spot.
For this reason, the best thing that you can do to protect yourself from malvertising attacks is to use an ad blocker. Ad blockers are software that blocks ads from being displayed on websites. This can help to prevent malicious ads from being displayed, as well as block other types of unwanted ads.
Another good way to protect yourself is to be cautious when clicking on ads. If an ad looks suspicious or too good to be true, it’s probably best to avoid clicking on it.
How to avoid ransomware and drive-by downloads?
When it comes to drive-by downloads, the best defense is a good offense. This means that you need to take proactive steps to protect yourself from these types of attacks.
One of the best things you can do is to use a reputable antivirus program and keep it up to date. Antivirus programs can help to identify and block malicious files before they can be executed.
Another good defense against drive-by downloads is to disable Java and JavaScript in your web browser. These are two of the most common ways that attackers exploit vulnerabilities to deliver malicious code. By disabling them, you can make it more difficult for attackers to infect your device successfully.
What to do if you are already infected by ransomware?
Now knowing all these tips to avoid ransomware, what do you do if you find yourself infected?
Unfortunately, once your device has been infected with ransomware, there is no guaranteed way to remove it. This is because the attackers usually have full control of your device and can encrypt your files in a way that makes them inaccessible.
If you find yourself in this situation, your best bet is to contact a professional who can help you to remove the ransomware and restore your files. In some cases, it may also be possible to pay the ransom and get a decryption key from the attacker. However, this is not recommended as it encourages them to continue their attacks and there’s no guarantee that you’ll get the key.
The best way to protect yourself from ransomware is to take proactive steps to prevent it from being installed in the first place. By following the tips in this guide, you can help to keep your device safe from this increasingly common type of attack.
FAQs
How can I tell if I have ransomware?
If you find that you are unable to access your files, or if they have been renamed with a strange extension, you may have been infected with ransomware.
Of course, the real confirmation is whether or not you receive a ransom demand.
How do I remove ransomware?
There is no guaranteed way to remove ransomware, but you may be able to use a professional service to help you. In some cases, it may also be possible to pay the ransom and get a decryption key from the attacker. That said, there’s no guarantee that this will work and it’s not recommended as it encourages them to continue their attacks.
Does VPN prevent ransomware?
A VPN can help to prevent ransomware by encrypting your traffic and making it more difficult for attackers to deliver malicious code. Some VPNs also come with ad blockers and other security features that can help to further protect you from ransomware and other types of attacks.
That said, a VPN won’t be able to help if you inadvertently click on a malware link or download an infected file. For this reason, it’s important to use a trustworthy VPN like ClearVPN in conjunction with other security measures, such as staying vigilant when clicking on links and using a reputable antivirus program.
So there you have it — our comprehensive guide to ransomware! We hope that this guide has helped to answer any questions that you may have had about this increasingly common type of attack.
Remember, the best way to protect yourself from ransomware is to take proactive steps to prevent it from being installed in the first place. By following the tips in this guide, you can help to keep your device safe from this dangerous threat.
